Mapping Kernel Memory to User Space: A Comprehensive Overview
Related Articles: Mapping Kernel Memory to User Space: A Comprehensive Overview
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Mapping Kernel Memory to User Space: A Comprehensive Overview. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Mapping Kernel Memory to User Space: A Comprehensive Overview
- 2 Introduction
- 3 Mapping Kernel Memory to User Space: A Comprehensive Overview
- 3.1 Understanding the Kernel and User Space Divide
- 3.2 Mapping Kernel Memory to User Space: Bridging the Divide
- 3.3 Benefits of Mapping Kernel Memory to User Space
- 3.4 Applications of Mapping Kernel Memory to User Space
- 3.5 Security Considerations
- 3.6 FAQs about Mapping Kernel Memory to User Space
- 3.7 Tips for Mapping Kernel Memory to User Space
- 3.8 Conclusion
- 4 Closure
Mapping Kernel Memory to User Space: A Comprehensive Overview
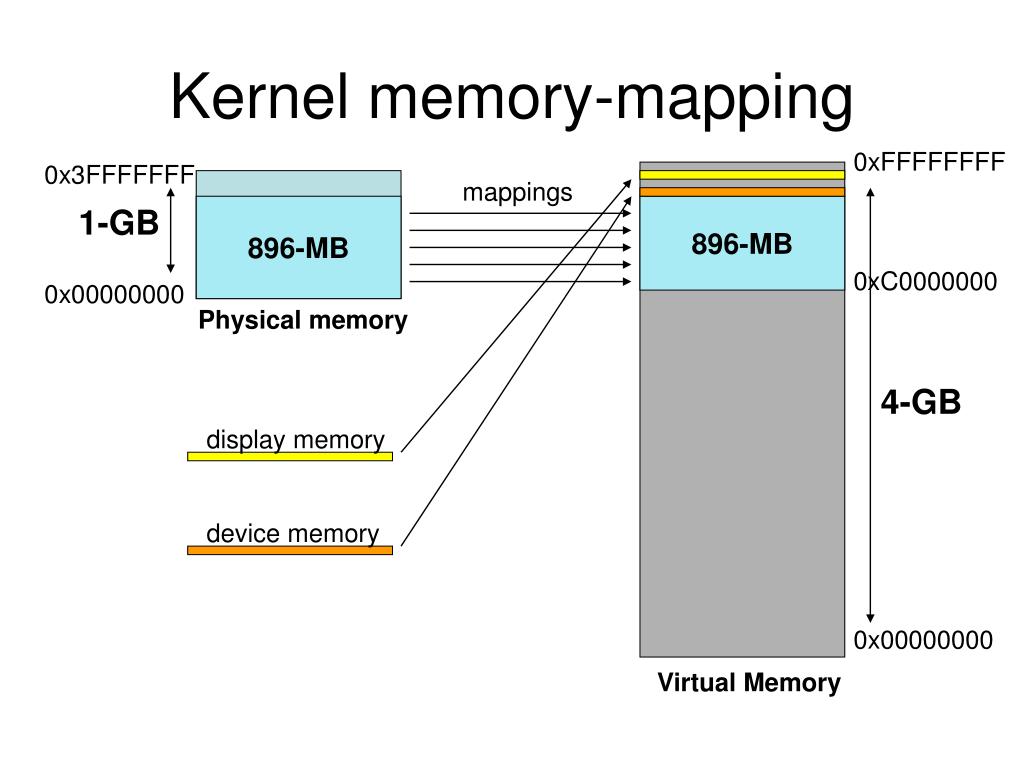
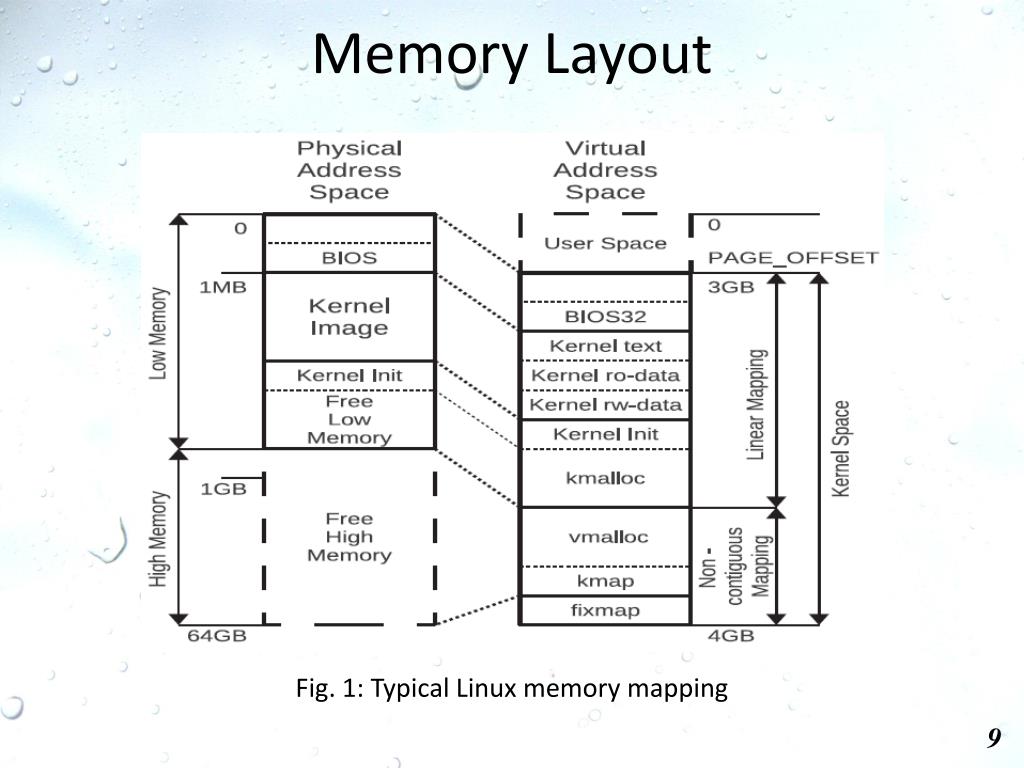
The ability to map kernel memory into user space is a powerful mechanism within operating systems, enabling efficient and secure communication between the kernel and user applications. This technique, often facilitated by the mmap system call, allows for direct access to kernel data structures and resources, bypassing the traditional overhead of system calls and copying data between kernel and user space. This article will delve into the intricacies of mapping kernel memory to user space, exploring its underlying principles, benefits, and practical applications.
Understanding the Kernel and User Space Divide
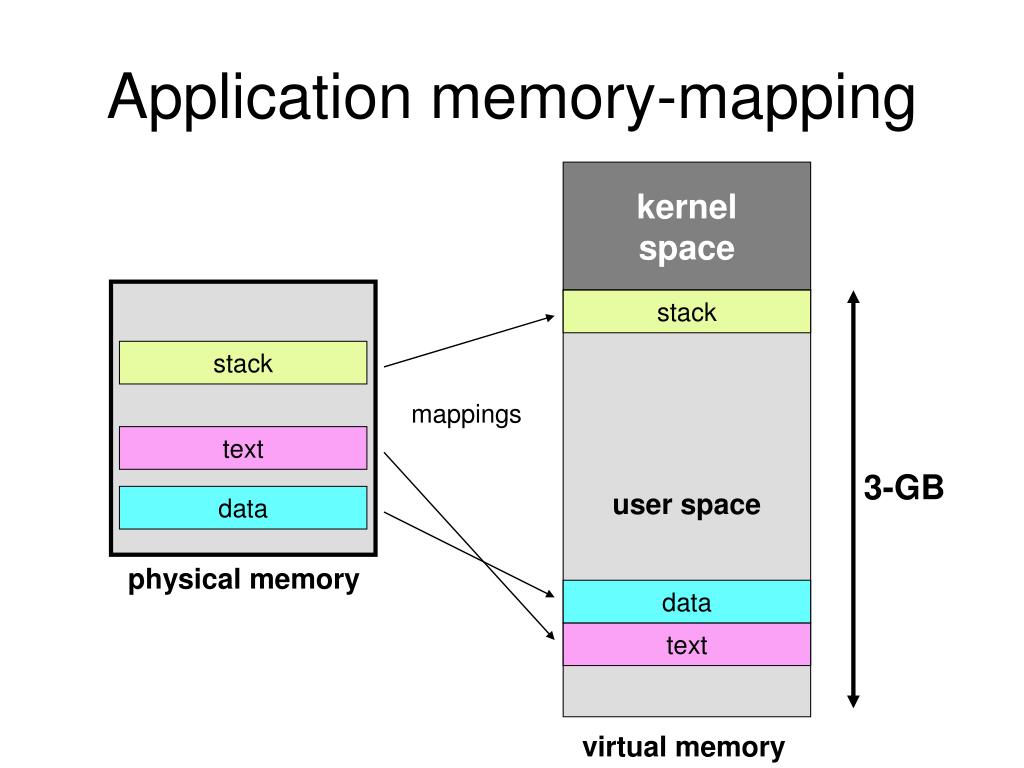
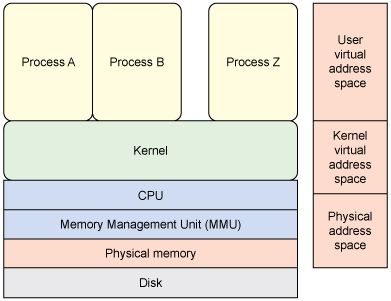
Operating systems implement a fundamental separation between the kernel and user space. The kernel, the core of the operating system, manages system resources, handles hardware interactions, and enforces security policies. User space, on the other hand, encompasses the applications and processes that users interact with. This separation ensures system stability and protects the kernel from malicious user programs.
However, this division presents a challenge when applications need to interact with kernel resources. Traditional methods rely on system calls, which involve a context switch from user space to kernel space, processing the request, and returning data to user space. This process is inherently slow and inefficient, especially for frequent data transfers.
Mapping Kernel Memory to User Space: Bridging the Divide
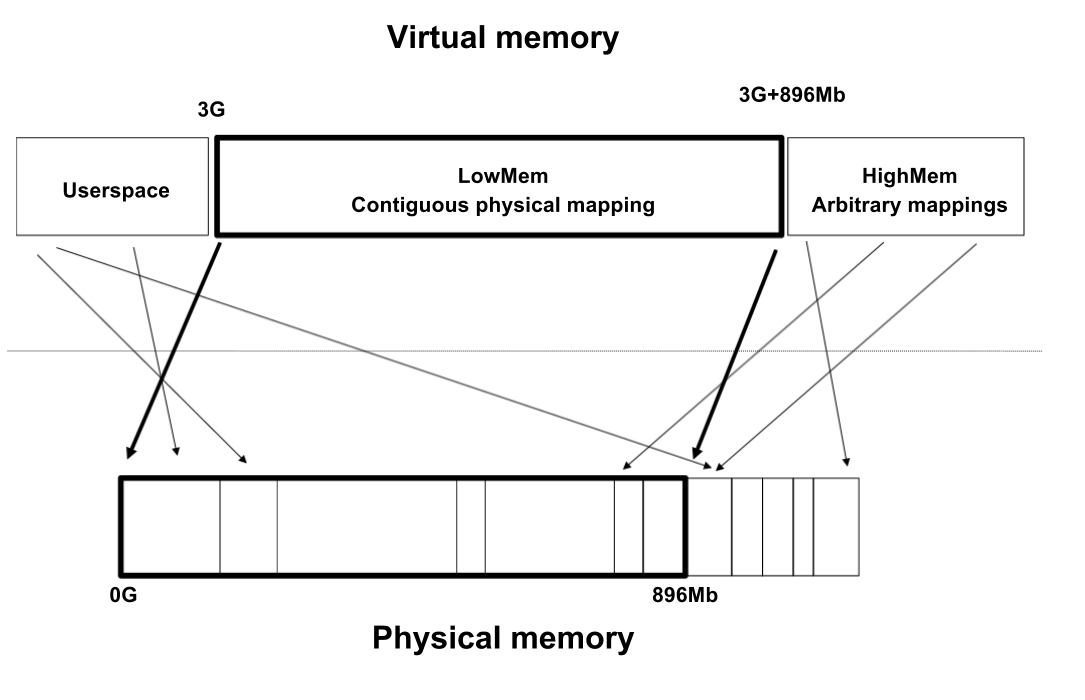
Mapping kernel memory to user space offers a more efficient and direct approach. This technique allows user applications to directly access kernel data structures and resources, effectively bypassing the overhead of system calls and data copying. The mmap system call, a key component of this process, establishes a virtual memory mapping between a region of kernel memory and a region of user space.
The mapping process involves the following steps:
- Kernel Allocation: The kernel allocates a memory region for the data or resource to be shared with user space.
-
Virtual Memory Mapping: The
mmapsystem call is invoked, specifying the kernel memory region and the desired user space address range. The operating system then establishes a virtual memory mapping between these two regions. - User Space Access: User applications can now directly access the kernel memory region through the mapped user space address range, as if it were their own memory.
Benefits of Mapping Kernel Memory to User Space
Mapping kernel memory to user space offers several significant benefits:
- Enhanced Performance: Direct access to kernel memory eliminates the need for system calls and data copying, resulting in significant performance improvements, particularly for frequent data transfers.
- Reduced Overhead: By reducing the number of system calls and data copies, this technique minimizes the overhead associated with user-kernel communication.
- Efficient Resource Management: Direct access to kernel data structures enables applications to manage resources more efficiently, without relying on system calls for every operation.
- Flexibility and Control: Applications can directly manipulate kernel data structures, providing greater flexibility and control over system resources.
Applications of Mapping Kernel Memory to User Space
Mapping kernel memory to user space finds applications in a wide range of areas, including:
- Device Drivers: Device drivers often need to access hardware resources managed by the kernel. Mapping kernel memory allows for efficient data transfer between the driver and the hardware.
- Network Protocols: Network protocols frequently require access to kernel-managed network buffers. Mapping kernel memory enables direct access to these buffers, improving network performance.
- File Systems: File systems utilize mapping to provide direct access to file data and metadata, enhancing file system performance.
- Performance Monitoring: Performance monitoring tools often need access to kernel data structures to gather system performance metrics. Mapping kernel memory allows for efficient data collection.
Security Considerations
While mapping kernel memory to user space offers significant benefits, it also introduces security risks. If not implemented carefully, this technique can lead to vulnerabilities that could be exploited by malicious applications.
- Kernel Data Corruption: Unauthorized access to kernel memory can lead to data corruption, potentially destabilizing the system.
- Privilege Escalation: Malicious applications could exploit vulnerabilities in the mapping process to gain elevated privileges, compromising system security.
To mitigate these risks, operating systems implement strict security measures:
- Access Control: Only authorized applications and processes are granted access to mapped kernel memory regions.
- Memory Protection: The operating system enforces memory protection mechanisms to prevent unauthorized access and modification of kernel data structures.
FAQs about Mapping Kernel Memory to User Space
1. What is the difference between mmap and system calls?
The mmap system call is a specific mechanism for mapping kernel memory to user space. It allows for direct access to kernel data structures and resources, bypassing the traditional overhead of system calls. System calls, on the other hand, are a general mechanism for user applications to request services from the kernel, involving a context switch and data copying.
2. Is mapping kernel memory to user space always secure?
No, mapping kernel memory to user space can introduce security risks if not implemented carefully. Unauthorized access can lead to data corruption and privilege escalation. Operating systems implement strict security measures to mitigate these risks.
3. What are the limitations of mapping kernel memory to user space?
- Security Risks: As mentioned above, unauthorized access can lead to security vulnerabilities.
- Complexity: Implementing and managing mapping requires careful consideration of security and performance trade-offs.
- Platform Dependence: The specific implementation and capabilities of mapping kernel memory to user space may vary across different operating systems and hardware platforms.
4. How can I learn more about mapping kernel memory to user space?
- Consult the documentation for your specific operating system.
- Explore online resources and tutorials on system programming and memory management.
- Study the source code of device drivers and other applications that utilize this technique.
Tips for Mapping Kernel Memory to User Space
- Plan carefully: Thoroughly understand the security implications and performance trade-offs before implementing mapping.
- Use appropriate security measures: Implement access control mechanisms and memory protection to prevent unauthorized access.
- Minimize the mapped memory region: Only map the necessary kernel memory to reduce the attack surface.
- Test thoroughly: Rigorously test your implementation to ensure its correctness and security.
Conclusion
Mapping kernel memory to user space offers a powerful mechanism for enhancing performance and efficiency in user-kernel communication. It enables direct access to kernel data structures and resources, bypassing the overhead of system calls and data copying. However, it’s essential to carefully consider the security implications and implement appropriate safeguards to prevent vulnerabilities. By understanding the benefits and challenges associated with this technique, developers can leverage its power while ensuring system stability and security.




Closure
Thus, we hope this article has provided valuable insights into Mapping Kernel Memory to User Space: A Comprehensive Overview. We appreciate your attention to our article. See you in our next article!