Memory Mapping: A Powerful Tool for Efficient Data Access
Related Articles: Memory Mapping: A Powerful Tool for Efficient Data Access
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Memory Mapping: A Powerful Tool for Efficient Data Access. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Memory Mapping: A Powerful Tool for Efficient Data Access
- 2 Introduction
- 3 Memory Mapping: A Powerful Tool for Efficient Data Access
- 3.1 Understanding the Fundamentals
- 3.2 The Mechanics of Memory Mapping
- 3.3 The Advantages of Memory Mapping
- 3.4 Common Applications of Memory Mapping
- 3.5 FAQs about Memory Mapping
- 3.6 Tips for Using Memory Mapping Effectively
- 3.7 Conclusion
- 4 Closure
Memory Mapping: A Powerful Tool for Efficient Data Access
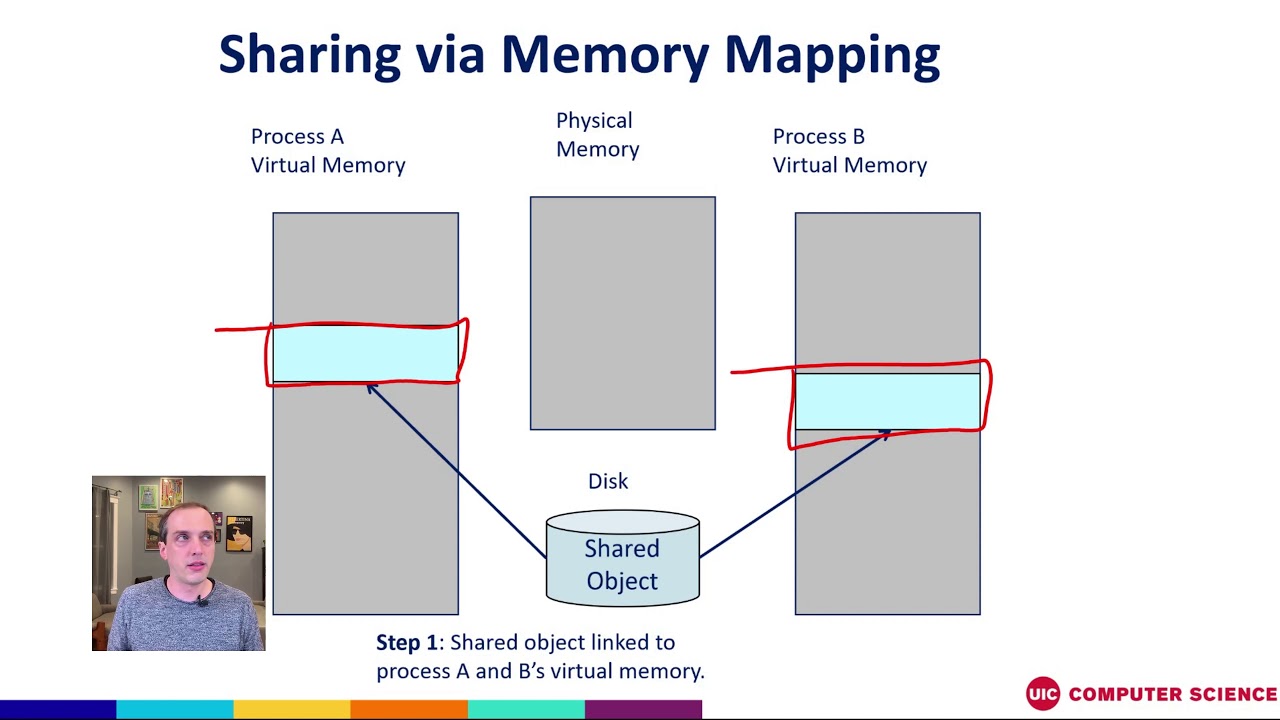
Memory mapping, often referred to as mmap, is a powerful mechanism that allows processes to access files as if they were directly in memory. This technique offers a significant advantage in terms of efficiency and performance, particularly when dealing with large datasets or frequent file I/O operations.
Understanding the Fundamentals
At its core, memory mapping establishes a direct mapping between a region of a process’s virtual address space and a file on disk. This mapping allows the process to read and write to the file as if it were a contiguous block of memory.
Key Features of Memory Mapping:
- Direct Access: Memory mapping eliminates the need for explicit read and write system calls, as data can be accessed directly through the mapped memory region.
- Shared Memory: Memory mapping facilitates shared memory access between multiple processes, enabling efficient communication and data sharing.
- Demand Paging: Data is only loaded into memory on demand, reducing memory footprint and improving system responsiveness.
- Efficient Data Transfer: The operating system handles the data transfer between disk and memory transparently, optimizing data movement and reducing the overhead associated with traditional file I/O.
The Mechanics of Memory Mapping
The process of memory mapping involves several key steps:
- File Opening: The process opens the target file using the standard file opening functions.
- Memory Allocation: The operating system allocates a region of virtual memory for the file mapping.
-
Mapping Creation: The
mmapsystem call is used to establish the mapping between the allocated memory region and the file. This call typically takes arguments specifying the file descriptor, the desired memory size, the mapping mode (read-only, write-only, or read-write), and other optional flags. - Data Access: The process can now access the file data directly through the mapped memory region, treating it as a standard memory buffer.
-
Mapping Removal: When the process is finished with the file, it should unmap the memory region using the
munmapsystem call to release the resources.
The Advantages of Memory Mapping
Memory mapping offers several significant advantages over traditional file I/O methods:
- Performance Enhancement: By eliminating the overhead associated with system calls and data copying, memory mapping significantly improves the speed of file access, especially for large files and frequent I/O operations.
- Reduced Memory Footprint: Demand paging ensures that only the required data is loaded into memory, minimizing the memory overhead and improving system efficiency.
- Simplified Data Handling: Memory mapping simplifies data access and manipulation, allowing processes to treat files as memory buffers and apply standard memory operations.
- Shared Memory Communication: Memory mapping provides a mechanism for efficient communication and data sharing between multiple processes, enabling parallel processing and collaborative tasks.
Common Applications of Memory Mapping
Memory mapping finds wide application in various domains, including:
- Database Systems: Databases often employ memory mapping to improve the performance of data access and caching.
- Image and Video Processing: Memory mapping is used for efficient loading and manipulation of large image and video files.
- Web Servers: Web servers utilize memory mapping to optimize the handling of static content and improve response times.
- Scientific Computing: Memory mapping is essential for high-performance computing applications involving large datasets and complex calculations.
- Operating Systems: Memory mapping plays a crucial role in the implementation of virtual memory systems, facilitating efficient memory management.
FAQs about Memory Mapping
Q: What are the different mapping modes available in mmap?
A: Memory mapping offers different modes depending on the intended use:
- MAP_SHARED: Changes made to the mapped memory region are visible to all processes that share the mapping.
- MAP_PRIVATE: Changes made to the mapped memory region are private to the process and do not affect other processes.
- MAP_ANONYMOUS: This mode allows mapping a region of memory without associating it with a file. This is useful for creating shared memory segments between processes.
Q: What are the potential drawbacks of memory mapping?
A: While memory mapping offers significant benefits, it also has some limitations:
- Memory Consumption: Mapping large files can consume significant memory resources, especially if the entire file is loaded into memory.
- Synchronization Issues: When using shared mappings, synchronization mechanisms are crucial to prevent race conditions and ensure data consistency.
- File System Limitations: Memory mapping may not be suitable for all file systems, particularly those with limited support for memory-mapped files.
Q: How does memory mapping handle file updates?
A: When changes are made to the mapped memory region, the operating system typically keeps track of these changes and writes them back to the file on disk when the mapping is unmapped or when the process terminates. However, the specific behavior can vary depending on the operating system and the mapping mode.
Q: Can memory mapping be used for creating shared memory segments?
A: Yes, memory mapping can be used to create shared memory segments by using the MAP_ANONYMOUS flag. This allows multiple processes to access and share a common memory region without relying on a physical file.
Tips for Using Memory Mapping Effectively
- Optimize File Size: For optimal performance, consider mapping only the relevant portion of the file, rather than the entire file.
- Utilize Synchronization: When working with shared mappings, implement appropriate synchronization mechanisms to ensure data consistency and avoid race conditions.
- Choose the Appropriate Mapping Mode: Carefully select the mapping mode based on the specific requirements of the application, considering factors like data sharing and visibility.
- Release Resources Properly: Ensure that you unmap the memory region when it is no longer needed to release resources and prevent memory leaks.
Conclusion
Memory mapping is a powerful and versatile technique that offers significant advantages for applications involving frequent file I/O operations or large datasets. By eliminating the overhead associated with traditional file I/O and providing efficient access to data, memory mapping can significantly improve performance and efficiency. However, it is crucial to understand the potential limitations and implement best practices to avoid issues like memory consumption and synchronization problems. With careful planning and execution, memory mapping can be a valuable tool for enhancing the performance and efficiency of applications across various domains.
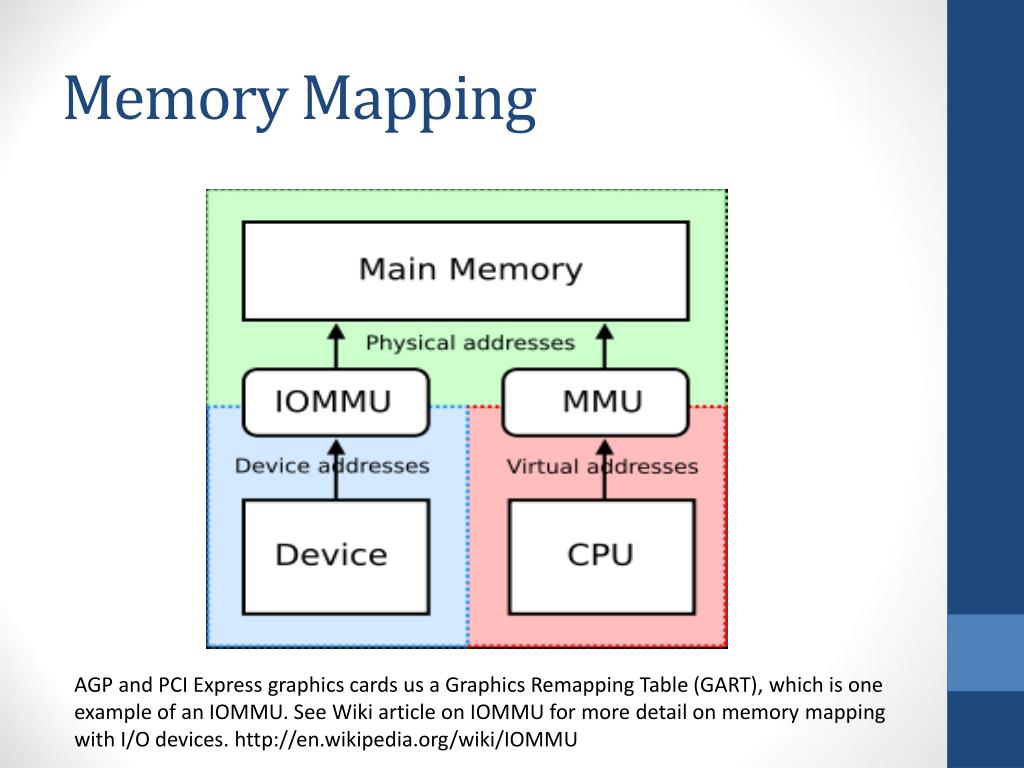




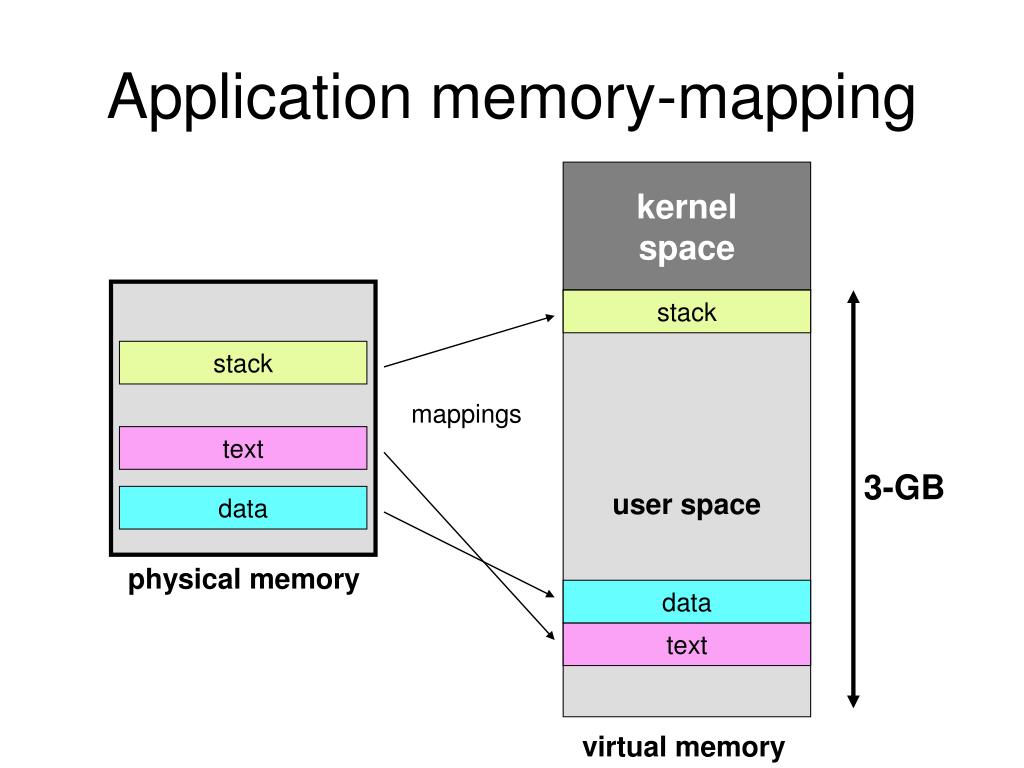
Closure
Thus, we hope this article has provided valuable insights into Memory Mapping: A Powerful Tool for Efficient Data Access. We hope you find this article informative and beneficial. See you in our next article!