Memory Mapping: Unlocking Efficiency and Flexibility in Modern Computing
Related Articles: Memory Mapping: Unlocking Efficiency and Flexibility in Modern Computing
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Memory Mapping: Unlocking Efficiency and Flexibility in Modern Computing. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Memory Mapping: Unlocking Efficiency and Flexibility in Modern Computing
- 2 Introduction
- 3 Memory Mapping: Unlocking Efficiency and Flexibility in Modern Computing
- 3.1 Understanding the Fundamentals of Memory Mapping
- 3.2 The Mechanics of Memory Mapping
- 3.3 Applications of Memory Mapping
- 3.4 Benefits of Memory Mapping
- 3.5 Considerations and Potential Drawbacks
- 3.6 Frequently Asked Questions
- 3.7 Tips for Effective Memory Mapping
- 3.8 Conclusion
- 4 Closure
Memory Mapping: Unlocking Efficiency and Flexibility in Modern Computing
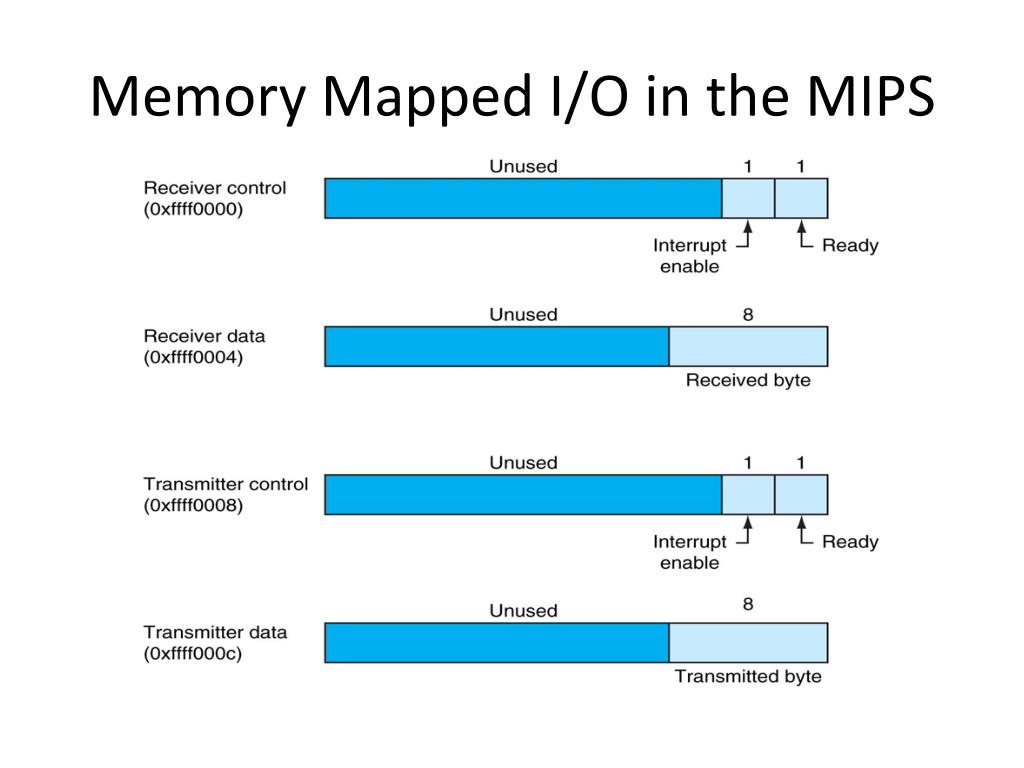
Memory mapping, a powerful technique employed in modern operating systems, offers a unique and efficient way to interact with files and data structures within a program’s memory space. This mechanism, often referred to as "memory-mapped files," allows applications to directly access and manipulate file contents as if they were residing in the program’s RAM, eliminating the need for traditional read and write operations. This approach significantly enhances performance, simplifies data handling, and unlocks possibilities for efficient resource management.
Understanding the Fundamentals of Memory Mapping
At its core, memory mapping establishes a direct connection between a file on disk and a region of the program’s virtual memory. This connection eliminates the need for explicit file I/O operations, allowing the program to treat the file’s data as if it were part of its own memory space. This seamless integration offers several advantages:
-
Direct Access: Programs can access any portion of the mapped file directly, bypassing the overhead of traditional file I/O operations. This eliminates the need to read or write entire blocks of data, significantly improving performance for tasks involving random access or frequent data modification.
-
Shared Memory: Memory mapping enables multiple processes to share access to the same file, facilitating efficient inter-process communication and data sharing. This eliminates the need for complex synchronization mechanisms, streamlining communication and collaboration between processes.
-
Reduced Memory Footprint: Memory mapping allows programs to access large files without loading the entire file into memory. This is particularly advantageous for handling large datasets, minimizing memory consumption and improving overall system efficiency.
The Mechanics of Memory Mapping
The process of memory mapping typically involves three key steps:
-
File Mapping: The program initiates a request to the operating system to map a specific file to a region of its virtual memory. The operating system allocates a virtual memory region and establishes a connection between this region and the file on disk.
-
Memory Access: Once the file is mapped, the program can access the file’s data directly through the allocated memory region. This access is transparent to the program, allowing it to treat the file data as if it were regular memory.
-
Unmapping: When the program no longer requires access to the mapped file, it can unmap the file from its virtual memory space. This releases the allocated memory region and terminates the connection between the file and the program’s memory.
Applications of Memory Mapping
Memory mapping finds widespread use in diverse applications, including:
-
Database Management: Memory mapping enables databases to access large data files efficiently, minimizing I/O operations and enhancing performance.
-
Image and Video Processing: Applications involving image and video processing can leverage memory mapping to access and manipulate large image and video files directly in memory, improving processing speed and responsiveness.
-
Scientific Computing: Scientific simulations and analyses often involve handling large datasets. Memory mapping allows these applications to access and process data efficiently, accelerating computations and improving accuracy.
-
Web Servers: Web servers can use memory mapping to efficiently serve static content, reducing disk access and improving response times.
-
Text Editors and IDEs: Text editors and integrated development environments (IDEs) utilize memory mapping to load and manipulate large code files, enabling fast editing and navigation.
Benefits of Memory Mapping
The use of memory mapping offers numerous benefits, enhancing application performance and efficiency:
-
Improved Performance: Direct access to file data eliminates the overhead of traditional file I/O operations, leading to significant performance improvements.
-
Simplified Data Handling: Memory mapping allows programs to treat files as if they were part of their own memory space, simplifying data access and manipulation.
-
Reduced Memory Consumption: Memory mapping enables programs to access large files without loading the entire file into memory, minimizing memory usage and improving system efficiency.
-
Enhanced Inter-Process Communication: Shared memory capabilities facilitate efficient communication and data sharing between processes, streamlining collaborative tasks.
Considerations and Potential Drawbacks
While memory mapping offers significant advantages, it’s crucial to consider potential drawbacks and implement it strategically:
-
Memory Overhead: Memory mapping involves allocating virtual memory space for the mapped file. This can impact overall system performance, especially when dealing with very large files or multiple mapped files.
-
Synchronization Issues: When multiple processes share a mapped file, proper synchronization mechanisms are essential to prevent data corruption or race conditions.
-
System Dependencies: Memory mapping functionality is provided by the operating system, and its implementation may vary across different systems.
-
Security Considerations: Memory mapping can expose sensitive data if not implemented securely. Access control mechanisms and proper security practices are crucial to protect mapped files from unauthorized access.
Frequently Asked Questions
Q: What is the difference between memory mapping and file I/O?
A: Traditional file I/O involves explicit read and write operations to access file data. Memory mapping, on the other hand, establishes a direct connection between the file and the program’s memory space, allowing direct access to the file’s contents as if they were in memory.
Q: How does memory mapping affect system performance?
A: Memory mapping can significantly improve performance by eliminating the overhead of traditional file I/O operations. However, allocating virtual memory for mapped files can impact overall system performance, especially when dealing with large files.
Q: Is memory mapping suitable for all applications?
A: Memory mapping is not always the optimal solution. It’s best suited for applications that require frequent access to large files, random data access, or efficient inter-process communication.
Q: Are there any security concerns associated with memory mapping?
A: Yes, memory mapping can expose sensitive data if not implemented securely. It’s crucial to implement access control mechanisms and follow proper security practices to protect mapped files from unauthorized access.
Tips for Effective Memory Mapping
-
Optimize File Size: Consider mapping only the necessary portions of a file to minimize memory overhead.
-
Implement Proper Synchronization: When multiple processes share a mapped file, use appropriate synchronization mechanisms to prevent data corruption or race conditions.
-
Choose the Right Memory Mapping Functions: Different operating systems provide various functions for memory mapping. Select the appropriate functions based on the specific requirements of your application.
-
Manage Memory Usage: Monitor memory usage and unmap files when they are no longer needed to prevent excessive memory consumption.
-
Prioritize Security: Implement robust security measures to protect mapped files from unauthorized access and ensure data integrity.
Conclusion
Memory mapping presents a powerful and efficient technique for interacting with files and data structures within a program’s memory space. It offers numerous benefits, including improved performance, simplified data handling, reduced memory consumption, and enhanced inter-process communication. While memory mapping is a valuable tool, it’s crucial to consider potential drawbacks, implement it strategically, and address security concerns to maximize its effectiveness and ensure the integrity of your applications. By understanding the fundamentals, benefits, and considerations of memory mapping, developers can harness its power to create efficient, responsive, and robust applications that effectively manage resources and optimize performance.

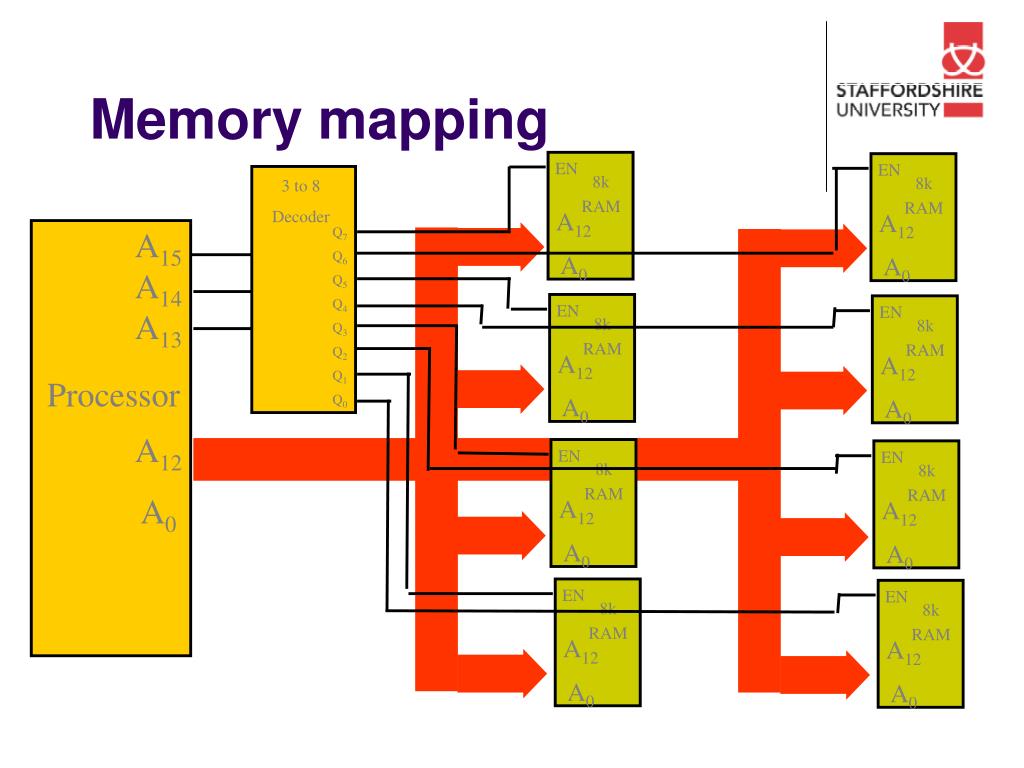

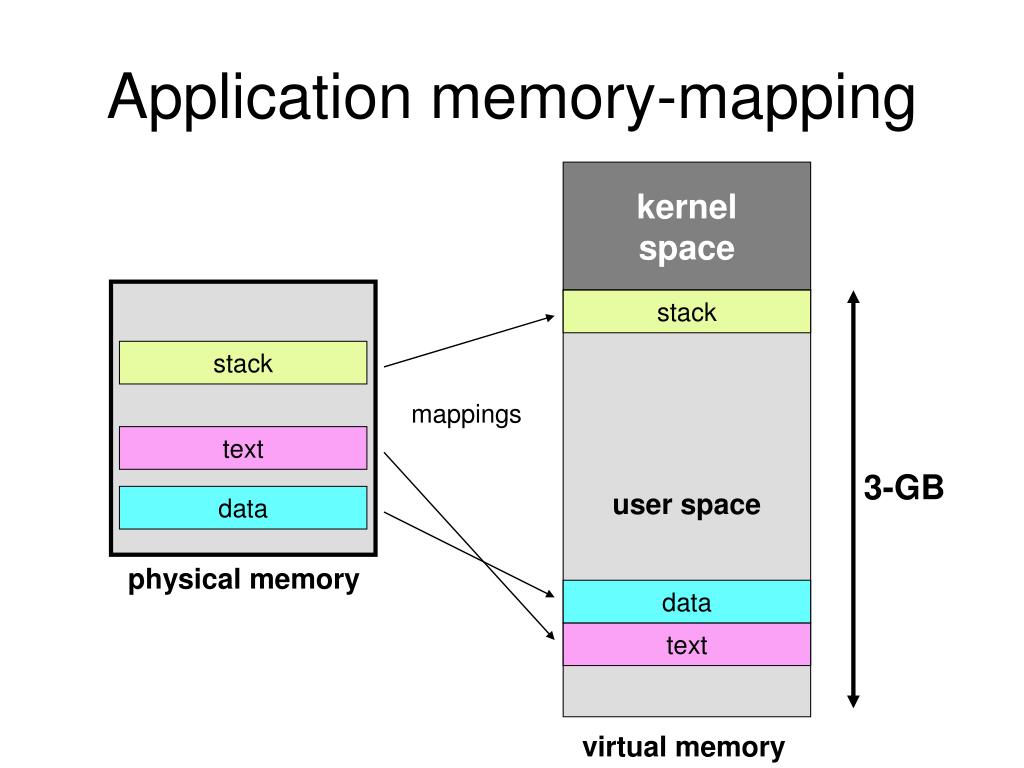
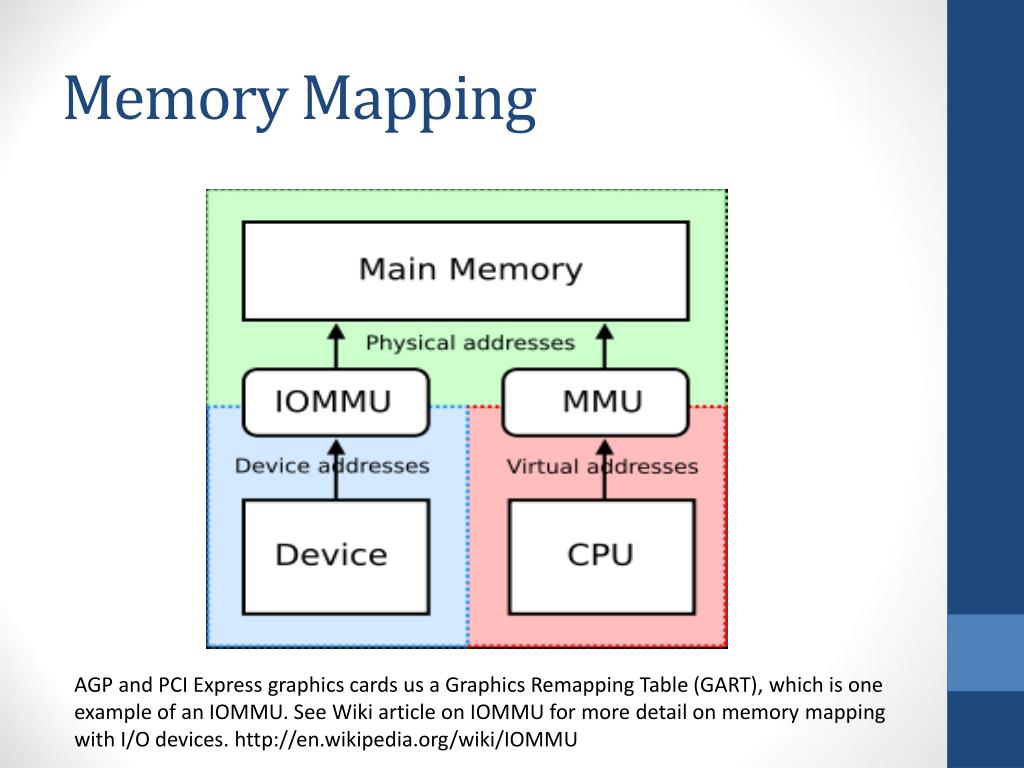

Closure
Thus, we hope this article has provided valuable insights into Memory Mapping: Unlocking Efficiency and Flexibility in Modern Computing. We thank you for taking the time to read this article. See you in our next article!
