Nmap: A Powerful Tool for Network Exploration and Security Auditing
Related Articles: Nmap: A Powerful Tool for Network Exploration and Security Auditing
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Nmap: A Powerful Tool for Network Exploration and Security Auditing. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Nmap: A Powerful Tool for Network Exploration and Security Auditing
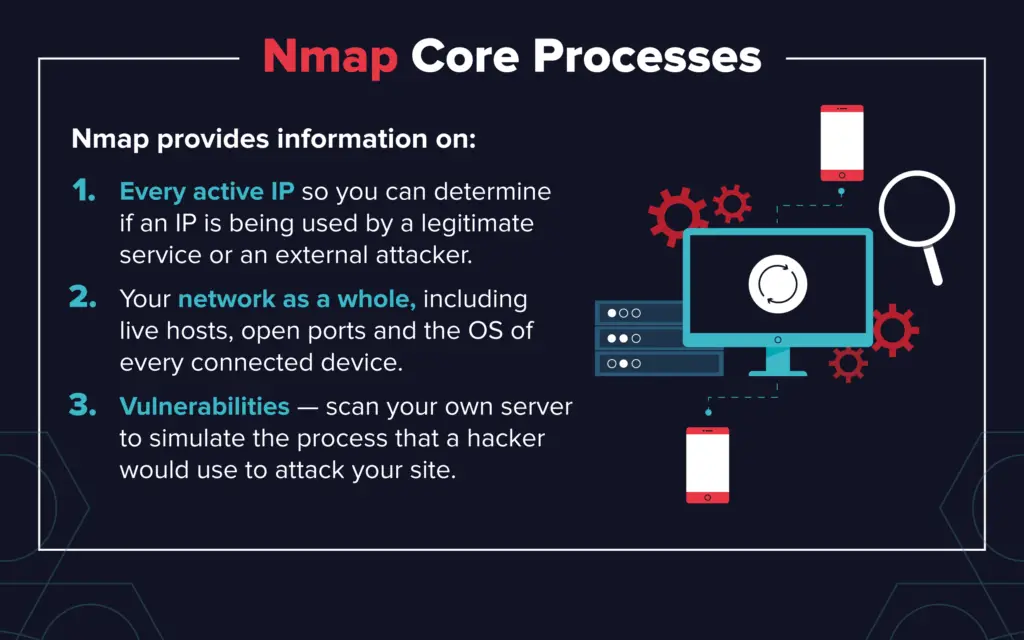
Nmap, short for Network Mapper, is a free and open-source utility that has become an indispensable tool for network administrators, security professionals, and researchers worldwide. It offers a comprehensive suite of features for network discovery, host and service identification, vulnerability scanning, and much more. This article delves into the capabilities of Nmap, exploring its functionalities, applications, and significance in the realm of network security.
Understanding the Core Functionalities of Nmap
Nmap’s primary function is to scan networks and gather information about the hosts and services present within them. This information can be used for various purposes, including:
- Network Discovery: Identifying active hosts on a network, determining their operating systems, and mapping the network topology.
- Service Identification: Identifying the services running on each host, their versions, and potential vulnerabilities.
- Security Auditing: Assessing the security posture of a network by identifying open ports, vulnerabilities, and misconfigurations.
- Network Troubleshooting: Diagnosing network connectivity issues, identifying potential bottlenecks, and resolving network problems.
Nmap’s Diverse Scanning Techniques
Nmap employs a variety of scanning techniques to achieve its goals. These techniques cater to different requirements and provide flexibility in customizing scans for specific purposes:
- TCP Connect Scan: This technique establishes a full TCP connection to each port, providing a reliable way to determine open ports.
- SYN Scan (Half-Open Scan): This technique sends a SYN packet to each port, mimicking a connection attempt without completing the handshake. It is faster than the TCP Connect Scan but may not be as reliable.
- UDP Scan: This technique sends UDP packets to each port, allowing for the detection of UDP services.
- FIN Scan: This technique sends a FIN packet to each port, which is typically ignored by firewalls. This allows for stealthy port scanning but may not be accurate in all cases.
- Null Scan: This technique sends a packet with all flags set to zero. It is considered stealthy as it does not elicit a response from the target.
Beyond Basic Scanning: Nmap’s Advanced Capabilities
Nmap’s functionalities extend far beyond basic port scanning. It offers a plethora of advanced features that enhance its capabilities and cater to diverse needs:
- Operating System Detection: Nmap can identify the operating systems running on target hosts by analyzing network responses and comparing them to its internal database.
- Version Detection: Nmap can identify the versions of services running on target hosts, allowing for targeted vulnerability assessments.
- Script Scanning: Nmap can execute scripts against target hosts to perform specific tasks, such as vulnerability checks, service enumeration, and banner grabbing.
- Network Mapping: Nmap can create network maps that visualize the network topology, including the connections between hosts and the services they offer.
- Network Time Synchronization: Nmap can synchronize the clocks of multiple hosts, ensuring accurate timing for network operations.
- Host Discovery: Nmap can identify active hosts on a network, even those that are not actively responding to scans.
Real-World Applications of Nmap
Nmap’s versatility makes it applicable in a wide range of scenarios, including:
- Network Security Auditing: Identifying vulnerabilities, misconfigurations, and potential security threats within a network.
- Vulnerability Scanning: Identifying known vulnerabilities in services and applications running on target hosts.
- Penetration Testing: Simulating real-world attacks to assess the security posture of a network and identify potential weaknesses.
- Network Monitoring: Tracking network traffic, identifying suspicious activity, and detecting potential intrusions.
- Network Troubleshooting: Diagnosing network connectivity issues and identifying potential bottlenecks.
- Research and Development: Studying network behavior, analyzing network protocols, and developing new security tools.
Nmap: A Tool for Ethical Hacking and Responsible Network Security
Nmap is a powerful tool that can be used for both ethical and unethical purposes. It is essential to use Nmap responsibly and ethically. Its capabilities should only be used for legitimate purposes, such as network security auditing, penetration testing, and research. Using Nmap for malicious activities, such as unauthorized network access or denial-of-service attacks, is illegal and unethical.
Understanding Nmap’s Command-Line Interface
Nmap is primarily a command-line tool, offering a flexible and powerful interface for executing scans and managing its functionalities. Users can customize scans by specifying target hosts, ports, scan techniques, and various options.
Essential Nmap Commands
-
nmap -sT <target>: Performs a TCP Connect Scan against the specified target. -
nmap -sS <target>: Performs a SYN Scan (Half-Open Scan) against the specified target. -
nmap -sU <target>: Performs a UDP Scan against the specified target. -
nmap -sV <target>: Performs a version scan to identify the versions of services running on the target. -
nmap -O <target>: Performs an operating system detection scan to identify the operating system running on the target. -
nmap -p <port_range> <target>: Scans the specified port range on the target. -
nmap -T4 <target>: Sets the scan timing to level 4, increasing the scan speed. -
nmap -A <target>: Performs a comprehensive scan, including OS detection, version detection, and script scanning.
Nmap’s Extensive Documentation and Community Support
Nmap boasts comprehensive documentation, including a user manual, tutorials, and FAQs. The Nmap project also has a vibrant community of users and developers who actively contribute to its development and provide support to other users.
Frequently Asked Questions (FAQs) about Nmap
Q: Is Nmap legal to use?
A: Nmap is legal to use for legitimate purposes, such as network security auditing, penetration testing, and research. However, using Nmap for malicious activities, such as unauthorized network access or denial-of-service attacks, is illegal and unethical.
Q: What are the benefits of using Nmap?
A: Nmap offers numerous benefits, including:
- Comprehensive network discovery and service identification capabilities.
- Powerful scanning techniques for various purposes.
- Advanced features for operating system detection, version detection, and script scanning.
- Flexibility and customization options for tailoring scans to specific needs.
- Extensive documentation and community support.
Q: How can I learn more about Nmap?
A: You can learn more about Nmap by exploring its official website, reading its documentation, and joining the Nmap community.
Tips for Effective Nmap Usage
- Start with basic scans: Begin by performing simple scans to understand the network and identify potential targets.
- Use specific scan techniques: Choose scan techniques that are appropriate for the specific task at hand.
- Customize scan options: Tailor scan options to achieve the desired results and minimize impact on the network.
- Analyze scan results: Carefully review scan results to identify vulnerabilities, misconfigurations, and potential security threats.
- Use Nmap scripts: Leverage Nmap scripts to automate tasks and perform specific scans.
- Stay updated: Keep Nmap up to date to benefit from new features and security enhancements.
Conclusion: Nmap’s Enduring Significance in Network Security
Nmap has evolved into an indispensable tool for network administrators, security professionals, and researchers. Its comprehensive capabilities, diverse scanning techniques, and advanced features make it a valuable asset for network exploration, security auditing, vulnerability assessment, and various other network-related tasks. As networks continue to grow in complexity and security threats become more sophisticated, Nmap’s role in ensuring network security will only become more crucial.


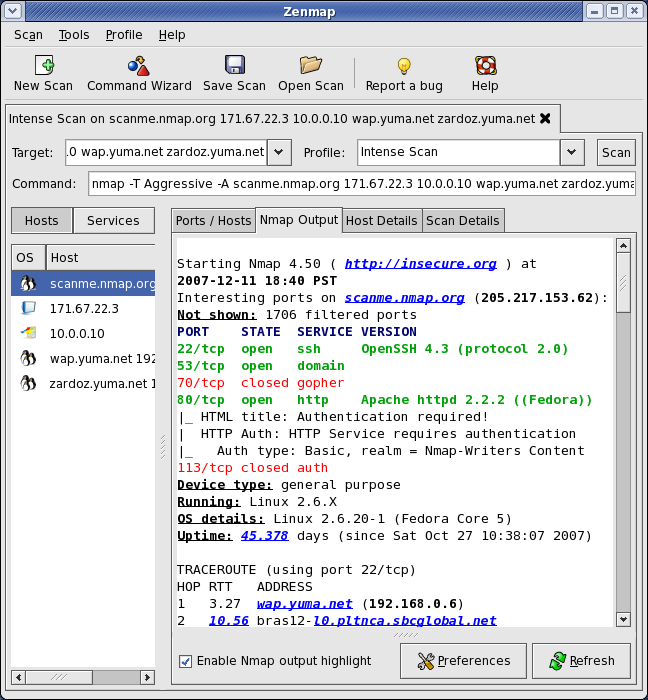
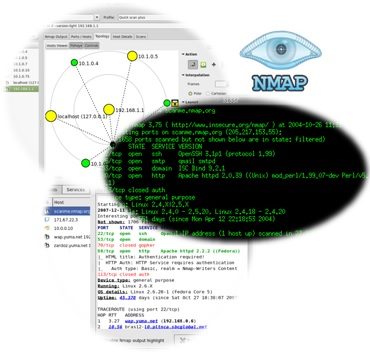


Closure
Thus, we hope this article has provided valuable insights into Nmap: A Powerful Tool for Network Exploration and Security Auditing. We hope you find this article informative and beneficial. See you in our next article!