Nmap: A Powerful Tool for Network Exploration and Security Auditing
Related Articles: Nmap: A Powerful Tool for Network Exploration and Security Auditing
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Nmap: A Powerful Tool for Network Exploration and Security Auditing. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Nmap: A Powerful Tool for Network Exploration and Security Auditing
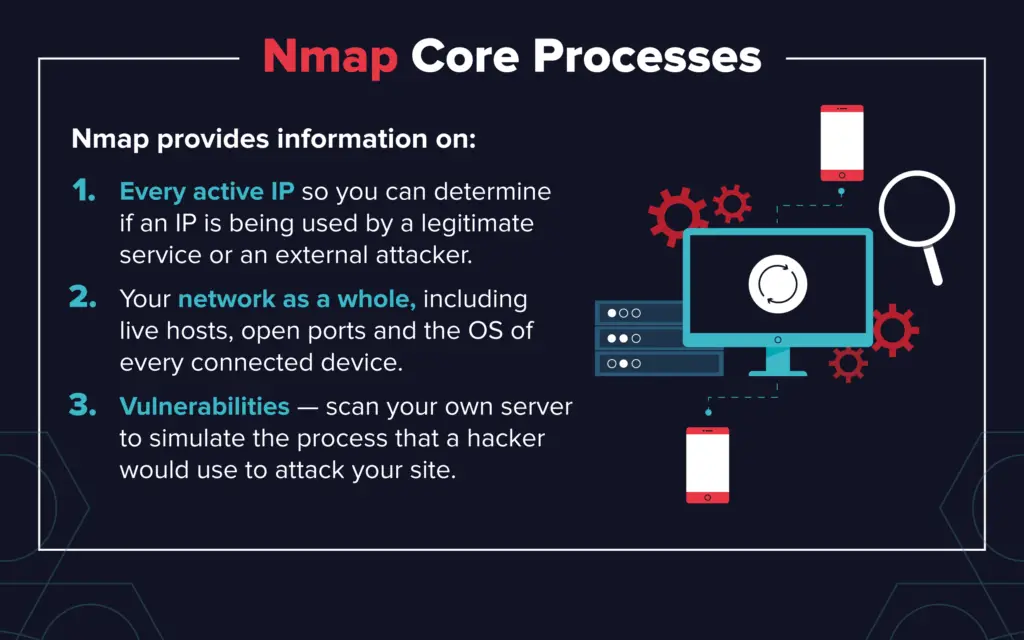
Nmap, short for Network Mapper, is a free and open-source utility used for network discovery and security auditing. It is a highly versatile tool, capable of performing a wide range of tasks, from identifying active hosts on a network to identifying vulnerabilities in systems.
Understanding the Basics of Network Scanning
Before diving into the intricacies of Nmap, it’s essential to understand the core concepts of network scanning. Network scanning involves sending probes to network devices to gather information about them. This information can include:
- Host Discovery: Identifying active devices on a network, including their IP addresses and MAC addresses.
- Port Scanning: Determining which ports on a host are open and listening for connections.
- Operating System (OS) Detection: Identifying the operating system running on a host.
- Service Detection: Identifying the services running on a host and their versions.
- Vulnerability Scanning: Identifying potential security weaknesses in systems.
Nmap’s Role in Network Exploration and Security Auditing
Nmap excels in performing these tasks efficiently and effectively. It offers a robust set of features that make it a powerful tool for:
- Network Discovery: Nmap can quickly and accurately identify active hosts on a network, even in large and complex environments. This is essential for network administrators to gain a comprehensive understanding of their network infrastructure.
- Security Auditing: Nmap can be used to identify potential security vulnerabilities in systems. By scanning for open ports and services, Nmap can detect misconfigurations and vulnerabilities that attackers could exploit.
- Network Mapping: Nmap can create detailed maps of network topologies, showing the connections between hosts and devices. This information can be invaluable for troubleshooting network issues and planning network upgrades.
- Network Monitoring: Nmap can be used to monitor network traffic and identify unusual activity. This can help to detect potential security threats and ensure network security.
Nmap’s Key Features and Capabilities
Nmap’s versatility stems from its extensive feature set, including:
- Flexible Scanning Techniques: Nmap supports a wide range of scanning techniques, including SYN scan, UDP scan, and TCP connect scan. These techniques allow users to tailor their scans to specific needs and security requirements.
- Script Engine: Nmap’s script engine allows users to extend Nmap’s functionality by running scripts that perform specific tasks, such as vulnerability scanning or service detection.
- Output Formats: Nmap can generate output in a variety of formats, including text, XML, and CSV. This makes it easy to share scan results with other tools and applications.
- Command-Line Interface: Nmap is primarily a command-line tool, offering users a high degree of control and customization.
- GUI Tools: While primarily command-line based, Nmap has GUI counterparts like Zenmap, offering a more user-friendly interface.
Nmap’s Applications in Various Fields
Nmap’s capabilities make it a valuable tool for a wide range of applications, including:
- Security Professionals: Nmap is a staple tool for security professionals, used for vulnerability scanning, penetration testing, and network security assessments.
- Network Administrators: Nmap aids network administrators in managing and monitoring their network infrastructure, identifying active devices, and troubleshooting connectivity issues.
- Researchers: Researchers use Nmap for network analysis, traffic analysis, and understanding network behavior.
- Developers: Nmap can assist developers in testing network applications and ensuring their security.
FAQs about Nmap
Q: Is Nmap legal to use?
A: Nmap is a legitimate tool used for security auditing and network exploration. However, its use may be restricted in certain situations, such as when scanning networks without permission. It’s crucial to adhere to local laws and ethical guidelines when using Nmap.
Q: Is Nmap dangerous?
A: Nmap itself is not dangerous. However, it can be used for malicious purposes if misused. It’s crucial to use Nmap responsibly and ethically, focusing on security assessments and legitimate network exploration.
Q: Can Nmap be used for hacking?
A: Nmap can be misused for malicious activities like port scanning, but its primary purpose is for security auditing and network exploration. It’s essential to use Nmap responsibly and ethically, adhering to legal and ethical guidelines.
Q: How can I learn Nmap?
A: Nmap offers extensive documentation, tutorials, and online resources. The official Nmap website, community forums, and online courses provide comprehensive guidance for learning Nmap.
Tips for Using Nmap Effectively
- Start with Basic Scans: Begin with basic scans to understand your network and gather initial information.
- Customize Scans: Tailor your scans to specific needs by adjusting scanning techniques, port ranges, and other parameters.
- Use Scripts: Utilize Nmap’s script engine to automate tasks and extend functionality.
- Analyze Results: Carefully analyze scan results to identify potential vulnerabilities and security risks.
- Stay Updated: Keep your Nmap installation up-to-date to benefit from the latest features and security patches.
Conclusion
Nmap is an indispensable tool for network exploration and security auditing. Its versatility, power, and ease of use make it a valuable asset for security professionals, network administrators, researchers, and developers. By understanding Nmap’s capabilities and using it responsibly, individuals can leverage its power to enhance network security and ensure a robust and secure digital environment.


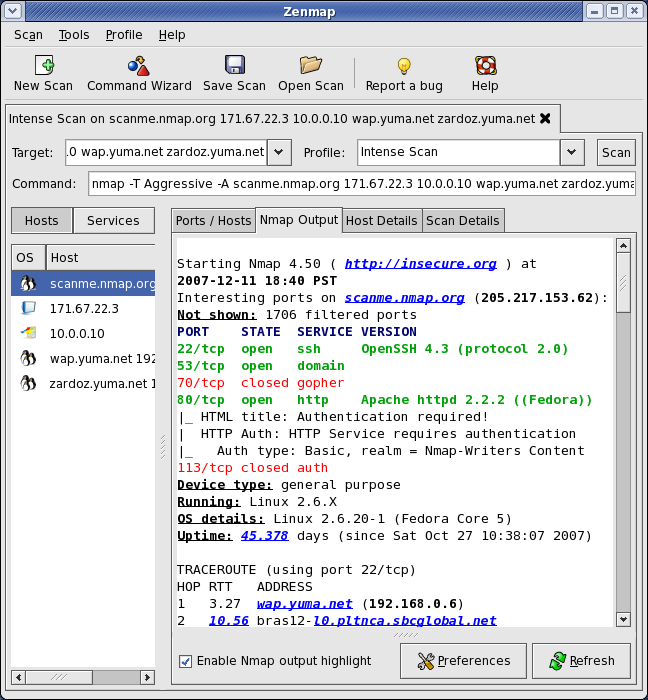
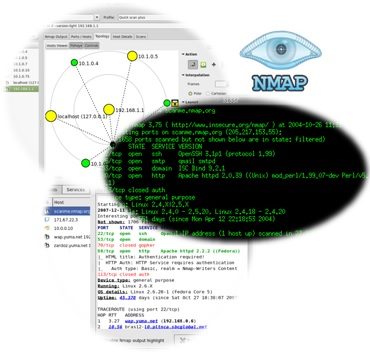


Closure
Thus, we hope this article has provided valuable insights into Nmap: A Powerful Tool for Network Exploration and Security Auditing. We appreciate your attention to our article. See you in our next article!