The Power of Memory Mapping: A Comprehensive Guide to Read-Only Access
Related Articles: The Power of Memory Mapping: A Comprehensive Guide to Read-Only Access
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to The Power of Memory Mapping: A Comprehensive Guide to Read-Only Access. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: The Power of Memory Mapping: A Comprehensive Guide to Read-Only Access
- 2 Introduction
- 3 The Power of Memory Mapping: A Comprehensive Guide to Read-Only Access
- 3.1 Understanding Memory Mapping
- 3.2 Read-Only Access: A Powerful Optimization Tool
- 3.3 Practical Applications of Read-Only Memory Mapping
- 3.4 Frequently Asked Questions about Read-Only Memory Mapping
- 3.5 Tips for Effective Use of Read-Only Memory Mapping
- 3.6 Conclusion
- 4 Closure
The Power of Memory Mapping: A Comprehensive Guide to Read-Only Access

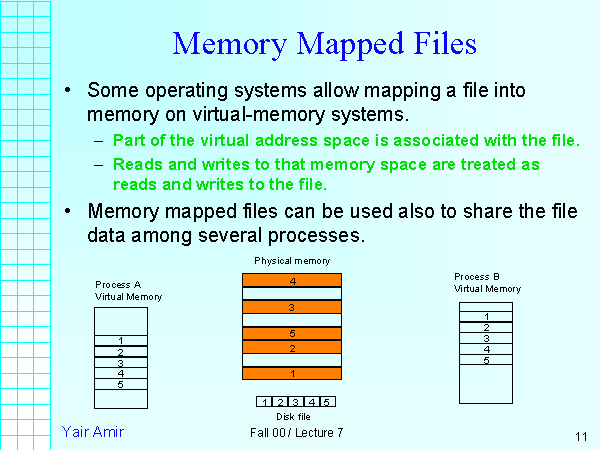
Memory mapping, a powerful technique employed in operating systems, provides a mechanism to directly access files within a program’s address space. This allows for efficient data manipulation, particularly when dealing with large files or when the need for random access is paramount. While memory mapping offers various benefits, focusing on the read-only aspect reveals its true potential for optimizing performance and enhancing security.
Understanding Memory Mapping
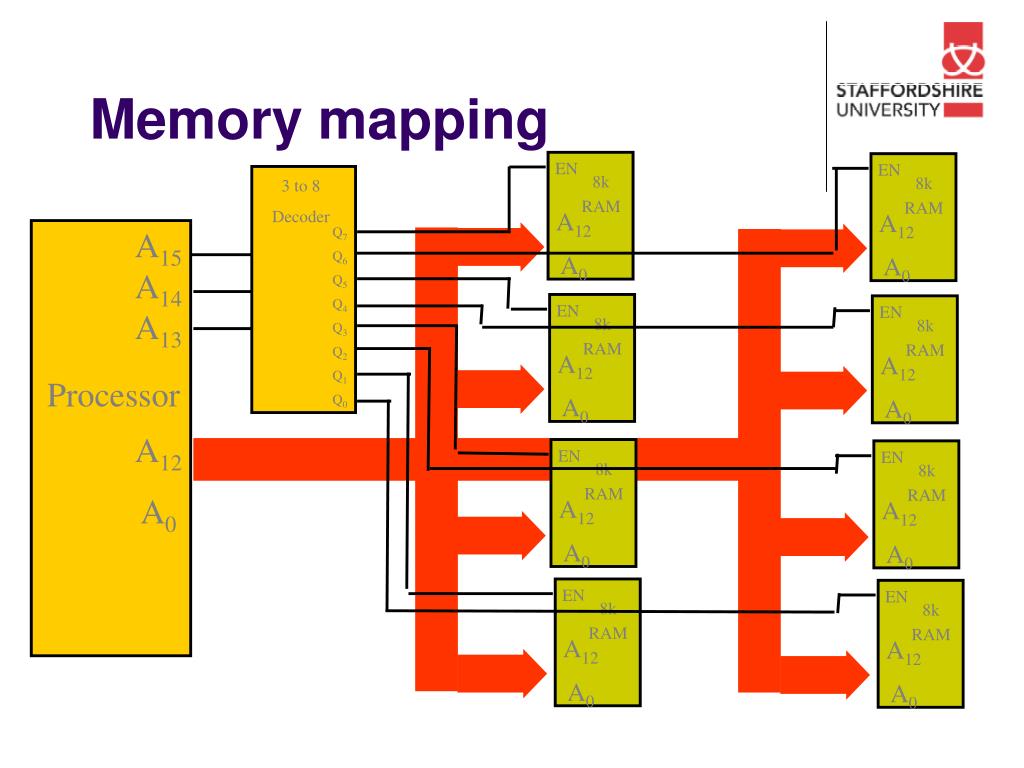
At its core, memory mapping establishes a direct link between a file residing on disk and a region of memory. This eliminates the need for traditional file I/O operations, which involve numerous system calls and data transfers between disk and memory. Instead, the operating system maps the file’s contents into the process’s virtual address space, allowing the program to treat the file as if it were directly in memory.
This approach streamlines data access, significantly reducing the overhead associated with conventional file operations. The benefits become particularly pronounced when dealing with large files, where the time required for disk access can be a significant performance bottleneck.
Read-Only Access: A Powerful Optimization Tool
When employing memory mapping in a read-only context, the operating system ensures that the mapped file cannot be modified by the program. This restriction safeguards the file’s integrity and prevents accidental or malicious changes.
Benefits of Read-Only Memory Mapping:
- Performance Enhancement: Read-only memory mapping eliminates the overhead associated with disk I/O operations, leading to substantial performance gains, especially when dealing with frequently accessed data.
- Security Enhancement: By preventing modifications to the mapped file, read-only memory mapping enhances security, ensuring data integrity and protecting against accidental or malicious alterations.
- Resource Optimization: Read-only memory mapping reduces the need for data copying, minimizing memory usage and optimizing resource allocation.
- Simplified Development: By treating files as memory regions, developers can focus on data processing rather than complex file handling operations, simplifying code and improving maintainability.
Practical Applications of Read-Only Memory Mapping
Read-only memory mapping finds its applications in various scenarios, including:
- Database Management Systems: Databases often utilize memory mapping to efficiently access large data files, improving query performance and reducing disk I/O overhead.
- Web Servers: Web servers leverage memory mapping to serve static content, such as images and HTML files, directly from memory, minimizing disk access and enhancing performance.
- Multimedia Applications: Applications dealing with large multimedia files, like video players or image editors, can significantly benefit from read-only memory mapping, reducing latency and improving responsiveness.
- Security Software: Antivirus and anti-malware programs often employ read-only memory mapping to analyze files without risking alteration, ensuring data integrity and preventing malicious modifications.
Frequently Asked Questions about Read-Only Memory Mapping
1. What are the limitations of read-only memory mapping?
While read-only memory mapping offers significant advantages, it’s essential to understand its limitations:
- Limited Flexibility: Read-only memory mapping restricts the ability to modify the mapped file. This may not be suitable for scenarios requiring data updates or modifications.
- Memory Overhead: Mapping large files into memory can consume a significant portion of available memory, potentially affecting system performance or leading to memory exhaustion.
- System Dependencies: The implementation and behavior of memory mapping can vary across different operating systems, requiring careful consideration for portability.
2. How can I determine if read-only memory mapping is suitable for my application?
The suitability of read-only memory mapping depends on several factors:
- File Size: For large files, memory mapping can offer significant performance advantages.
- Access Pattern: If your application primarily reads data, read-only memory mapping is a suitable choice.
- Data Modification: If data modification is required, read-only memory mapping may not be the most appropriate approach.
- System Resources: Consider the available memory resources and potential impact on system performance.
3. What are the best practices for using read-only memory mapping?
- Minimize Memory Usage: Carefully consider the size of the mapped file and the available memory resources to avoid memory exhaustion.
- Error Handling: Implement robust error handling mechanisms to manage potential errors during memory mapping operations.
- Security Considerations: Ensure that the mapped file is properly protected against unauthorized access or modifications.
- Performance Optimization: Optimize the memory mapping parameters to achieve optimal performance for your specific application.
Tips for Effective Use of Read-Only Memory Mapping
- Choose the Right Mapping Type: Different operating systems provide various memory mapping types. Select the type best suited for your application’s needs.
- Optimize Memory Allocation: Allocate memory for mapping based on the size of the file and available resources.
- Implement Error Handling: Handle potential errors during mapping operations to ensure robust application behavior.
- Monitor System Performance: Regularly monitor system performance to identify any potential issues related to memory mapping.
Conclusion
Read-only memory mapping presents a powerful technique for optimizing performance and enhancing security in applications that primarily access data without modification. By directly accessing files within the program’s address space, read-only memory mapping eliminates the overhead associated with traditional file I/O operations, leading to substantial performance gains. Moreover, the read-only nature of this approach safeguards data integrity, preventing accidental or malicious alterations.
Understanding the benefits, limitations, and best practices associated with read-only memory mapping empowers developers to leverage this powerful technique effectively, optimizing application performance, enhancing security, and simplifying development efforts.


Closure
Thus, we hope this article has provided valuable insights into The Power of Memory Mapping: A Comprehensive Guide to Read-Only Access. We appreciate your attention to our article. See you in our next article!