Understanding the Significance of Key Mapping Errors: A Comprehensive Guide
Related Articles: Understanding the Significance of Key Mapping Errors: A Comprehensive Guide
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Understanding the Significance of Key Mapping Errors: A Comprehensive Guide. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Understanding the Significance of Key Mapping Errors: A Comprehensive Guide
- 2 Introduction
- 3 Understanding the Significance of Key Mapping Errors: A Comprehensive Guide
- 3.1 Delving into the Concept of Maps and Keys
- 3.2 Why Keys Go Astray: Exploring the Causes of Invalid Map Keys
- 3.3 The Impact of Invalid Map Keys: A Ripple Effect
- 3.4 Mitigating the Risk: Strategies for Avoiding Invalid Map Keys
- 3.5 FAQs: Addressing Common Questions about Invalid Map Keys
- 3.6 Conclusion: Ensuring Data Integrity through Key Management
- 4 Closure
Understanding the Significance of Key Mapping Errors: A Comprehensive Guide
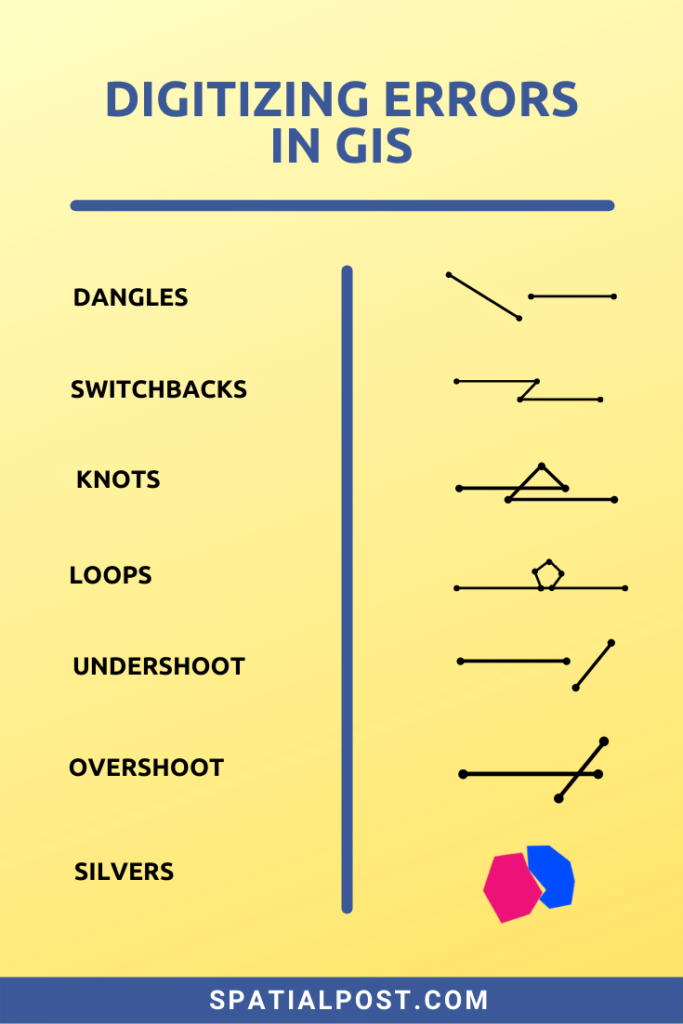
The term "invalid map k t key" is a technical phrase that arises in the context of computer programming and data manipulation. It refers to a situation where a specific key within a data structure, often a map or dictionary, is not recognized or cannot be accessed correctly. This error can manifest in various ways, leading to unexpected program behavior, data corruption, and system instability. Understanding the root causes and implications of this error is crucial for developers and data professionals to ensure the smooth functioning of applications and systems.
Delving into the Concept of Maps and Keys
Maps, also known as dictionaries, are fundamental data structures used in programming languages like Python, Java, and C++. They allow storing data in key-value pairs, enabling efficient retrieval of specific values based on their corresponding keys. Keys act as unique identifiers, much like addresses in a physical address book, while values hold the associated data.
For instance, consider a map representing the names and ages of individuals:
- Key: "John"
- Value: 30
This map stores the information that John is 30 years old. Accessing the age of John would require using the key "John" to retrieve the corresponding value, "30."
Why Keys Go Astray: Exploring the Causes of Invalid Map Keys
The "invalid map k t key" error occurs when a program attempts to access a key that is not present in the map or when the key is not in the expected format. This can happen due to several factors:
1. Typos and Misspellings: The most common cause of invalid keys is simply a typographical error. A single misspelling in the key can render it unrecognizable to the map, leading to an error.
2. Case Sensitivity: Some programming languages are case-sensitive, meaning that "John" and "john" are considered different keys. If the program attempts to access "john" while the map only contains "John," an invalid key error will result.
3. Data Type Mismatch: Each key in a map is typically associated with a specific data type. Trying to access a key using a different data type can cause an invalid key error. For example, if the map uses strings as keys, attempting to access it with an integer will likely lead to an error.
4. Key Duplicates: Most maps are designed to store unique keys. Attempting to insert a duplicate key can result in an invalid key error or overwrite the existing value associated with that key.
5. Missing Keys: If a program attempts to access a key that does not exist in the map, an invalid key error will occur. This can happen if the key was not added to the map previously or if it was accidentally deleted.
6. Key Manipulation: In some cases, invalid keys can arise from manipulating existing keys in a way that violates the map’s rules. This could involve modifying the key’s structure or changing its data type.
The Impact of Invalid Map Keys: A Ripple Effect
The consequences of an invalid map key error can be significant, ranging from minor inconveniences to severe system disruptions:
1. Program Crashes: The most severe outcome is a program crash. If the error occurs in a critical part of the code, the program may be unable to continue execution, leading to a complete shutdown.
2. Data Corruption: If the error occurs during data manipulation, it can lead to data corruption, where the wrong values are associated with the wrong keys. This can have disastrous consequences, especially in applications dealing with sensitive data.
3. Unexpected Behavior: Invalid map keys can also cause unexpected program behavior, where the program operates in ways that were not intended. This can lead to incorrect calculations, inaccurate output, and unpredictable responses.
4. System Instability: In extreme cases, invalid map keys can lead to system instability, causing the entire system to slow down, freeze, or even crash.
Mitigating the Risk: Strategies for Avoiding Invalid Map Keys
Preventing invalid map keys is paramount to ensuring the reliability and stability of software applications. Here are some strategies to minimize the occurrence of these errors:
1. Careful Coding: Pay meticulous attention to detail when coding, ensuring that all keys are spelled correctly and used consistently. Employ code analysis tools to help identify potential errors early on.
2. Data Validation: Implement data validation checks to ensure that all keys are in the expected format and data type before they are added to the map. This can prevent errors arising from typos, case sensitivity, and data type mismatches.
3. Key Management: Employ robust key management practices, including clearly defining key naming conventions, using unique identifiers, and avoiding duplication.
4. Map Initialization: Initialize maps with a predefined set of keys to ensure that all necessary keys are present and accessible.
5. Error Handling: Incorporate appropriate error handling mechanisms to gracefully handle invalid key errors. This can involve catching the exception, logging the error, and providing informative messages to the user.
6. Testing: Thoroughly test the application with various scenarios, including invalid key inputs, to identify and address potential issues before deployment.
FAQs: Addressing Common Questions about Invalid Map Keys
Q: What are the common symptoms of an invalid map k t key error?
A: Common symptoms include program crashes, unexpected program behavior, incorrect output, and error messages related to key access or manipulation.
Q: How can I debug an invalid map k t key error?
A: Debugging involves carefully examining the code, checking for typos, verifying data types, and using debugging tools to trace the execution flow and identify the source of the error.
Q: What are the best practices for preventing invalid map k t key errors?
A: Best practices include careful coding, data validation, key management, map initialization, error handling, and thorough testing.
Q: Are there any tools that can help identify invalid map keys?
A: Some programming languages and integrated development environments (IDEs) offer built-in tools for static code analysis, which can identify potential errors, including invalid map keys. Third-party tools and libraries also exist for code analysis and error detection.
Q: Can I use a generic key for all data in a map?
A: Using a generic key for all data is not recommended as it defeats the purpose of using a map. Maps are designed to store and retrieve data based on unique keys, allowing efficient access to specific data points.
Q: What are the alternatives to using maps?
A: If the specific requirements do not necessitate the use of maps, alternative data structures such as arrays or lists can be used. However, these structures may not offer the same efficiency for data retrieval based on keys.
Conclusion: Ensuring Data Integrity through Key Management
The "invalid map k t key" error, though seemingly simple, highlights the critical importance of meticulous data management and error prevention in software development. Understanding the causes and consequences of this error empowers developers to build robust and reliable applications. By implementing best practices for key management, data validation, and error handling, developers can significantly minimize the risk of these errors, ensuring the integrity and stability of their software systems.



Closure
Thus, we hope this article has provided valuable insights into Understanding the Significance of Key Mapping Errors: A Comprehensive Guide. We thank you for taking the time to read this article. See you in our next article!