Unlocking Network Security Insights: A Comprehensive Guide to Nmap Freebuf
Related Articles: Unlocking Network Security Insights: A Comprehensive Guide to Nmap Freebuf
Introduction
With great pleasure, we will explore the intriguing topic related to Unlocking Network Security Insights: A Comprehensive Guide to Nmap Freebuf. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Unlocking Network Security Insights: A Comprehensive Guide to Nmap Freebuf
- 2 Introduction
- 3 Unlocking Network Security Insights: A Comprehensive Guide to Nmap Freebuf
- 3.1 Understanding the Power of Nmap Freebuf
- 3.2 The Benefits of Nmap Freebuf
- 3.3 Unveiling the Functionality of Nmap Freebuf
- 3.4 Practical Applications of Nmap Freebuf
- 3.5 Addressing Frequently Asked Questions
- 3.6 Tips for Effective Nmap Freebuf Utilization
- 3.7 Conclusion: Empowering Network Security with Nmap Freebuf
- 4 Closure
Unlocking Network Security Insights: A Comprehensive Guide to Nmap Freebuf
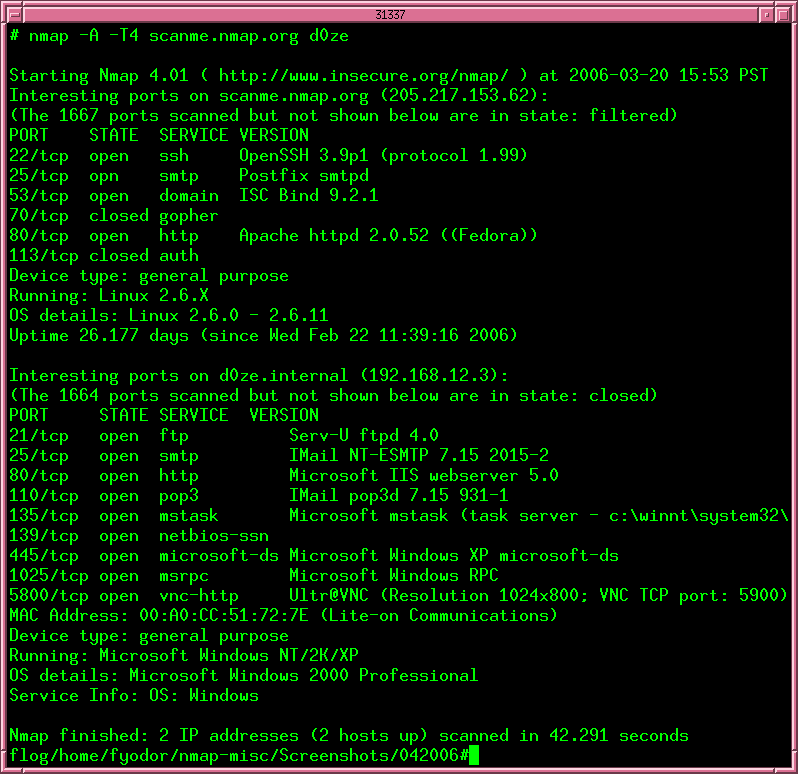
Nmap, the Network Mapper, is a powerful and versatile tool used by security professionals, network administrators, and system engineers worldwide. It provides an array of capabilities for network exploration, security auditing, and vulnerability assessment. One of its most valuable features is the ability to leverage freely available network intelligence data through the integration of "Freebuf" databases. This article delves into the world of Nmap Freebuf, exploring its functionality, benefits, and practical applications.
Understanding the Power of Nmap Freebuf
Nmap Freebuf is not a separate tool but rather a mechanism within Nmap that leverages external databases of network information to enrich scan results. These databases, often referred to as "Freebuf" sources, contain a wealth of publicly available information about networks, hosts, and services. By integrating this information, Nmap provides users with a more comprehensive and contextually relevant understanding of their target network.
The Benefits of Nmap Freebuf
The utilization of Freebuf data offers several distinct advantages for network security professionals and system administrators:
- Enhanced Network Discovery: Freebuf databases can reveal hidden hosts, services, and vulnerabilities that might otherwise remain undetected. This is particularly beneficial for large networks or environments with complex configurations.
- Improved Vulnerability Assessment: By correlating scan results with known vulnerabilities documented in Freebuf sources, Nmap can provide a more accurate and actionable picture of potential security risks. This allows for more targeted and efficient remediation efforts.
- Contextualized Network Analysis: Freebuf data provides valuable context, such as host names, operating systems, and service versions, which helps users understand the purpose and potential risks associated with individual systems within a network.
- Time and Resource Savings: Accessing Freebuf data eliminates the need for manual research and reduces the time required to gather crucial network information. This allows security professionals to focus on higher-level analysis and remediation tasks.
Unveiling the Functionality of Nmap Freebuf
The integration of Freebuf data within Nmap is facilitated through the use of specific command-line options and scripting capabilities. These options enable users to specify which Freebuf databases they want to use and how they want to integrate the information into their scans.
1. Specifying Freebuf Sources:
Users can define specific Freebuf sources using the --freebuf option. This allows for targeted data retrieval based on the type of information desired. For instance, users can specify sources like:
- Shodan: A popular search engine for internet-connected devices, providing insights into open ports, services, and device types.
- Censys: A platform for exploring the internet’s infrastructure, offering data on network devices, certificates, and vulnerabilities.
- OpenWRT: A community-driven open-source firmware for routers and other embedded devices, providing information on specific device models and their associated vulnerabilities.
2. Integrating Freebuf Data:
The retrieved Freebuf data is seamlessly integrated into Nmap’s output, providing users with a comprehensive and enriched view of their target network. This integration can be achieved through various methods, including:
- Displaying Freebuf Data: Nmap can display Freebuf data alongside scan results, such as host names, operating systems, and known vulnerabilities associated with specific hosts and services.
- Scripting and Automation: Nmap’s scripting capabilities allow users to automate the integration of Freebuf data into custom scripts and workflows, enabling efficient analysis and reporting.
- Customizing Output: Nmap offers flexible output options, allowing users to tailor the display of Freebuf data based on their specific needs and preferences.
Practical Applications of Nmap Freebuf
The integration of Freebuf data has numerous practical applications across various domains, including:
1. Network Security Auditing:
Nmap Freebuf can be leveraged to perform comprehensive security audits, identifying potential vulnerabilities, misconfigurations, and unauthorized devices within a network. By correlating scan results with known vulnerabilities documented in Freebuf sources, security professionals can prioritize remediation efforts and mitigate risks effectively.
2. Vulnerability Research and Exploitation:
Freebuf data can provide valuable insights into known vulnerabilities and their potential exploitability. Researchers and security professionals can utilize this information to identify and analyze vulnerabilities, develop exploit tools, and enhance their understanding of attack vectors.
3. Incident Response and Forensics:
During incident response investigations, Nmap Freebuf can help gather crucial information about compromised systems, including host names, operating systems, and potentially compromised services. This data can aid in identifying the source of the attack, understanding the attack vector, and mitigating the impact of the incident.
4. Penetration Testing and Red Teaming:
Penetration testers and red teams can leverage Nmap Freebuf to gather information about target networks, identify potential attack vectors, and plan their testing strategies. The information obtained from Freebuf sources can provide a valuable starting point for reconnaissance and vulnerability analysis.
Addressing Frequently Asked Questions
1. What are the potential risks associated with using Freebuf data?
While Freebuf data can provide valuable insights, it is essential to be aware of potential risks. As this data is publicly available, it may be outdated or inaccurate. Additionally, some Freebuf sources may contain sensitive information that could be misused. It is crucial to use Freebuf data responsibly and validate its accuracy before making critical decisions.
2. How can I ensure the accuracy of Freebuf data?
While Freebuf data can be valuable, it is essential to validate its accuracy before making critical decisions. Cross-referencing information from multiple sources, verifying information with other tools, and consulting with security experts can help ensure the reliability of the data.
3. Are there any legal implications associated with using Freebuf data?
The legality of using Freebuf data can vary depending on the specific source, the intended use, and the applicable laws and regulations. It is essential to research and comply with relevant legal frameworks before using Freebuf data for any purpose.
4. How can I effectively utilize Nmap Freebuf for my specific needs?
The effective use of Nmap Freebuf depends on the specific goals and requirements of the user. It is essential to understand the available Freebuf sources, the types of information they provide, and how to integrate this data into Nmap scans. Consulting with security experts and exploring Nmap’s documentation can help users leverage this powerful feature effectively.
Tips for Effective Nmap Freebuf Utilization
- Choose the right Freebuf sources: Select sources that align with your specific needs and provide relevant information for your target network.
- Validate data accuracy: Cross-reference information from multiple sources and verify data with other tools to ensure its reliability.
- Integrate Freebuf data effectively: Leverage Nmap’s scripting capabilities to automate the integration of Freebuf data into custom workflows and analysis processes.
- Use Freebuf data responsibly: Be mindful of potential risks associated with using publicly available data and comply with relevant legal frameworks.
Conclusion: Empowering Network Security with Nmap Freebuf
Nmap Freebuf empowers security professionals, network administrators, and system engineers with a powerful tool for enhancing network security analysis and vulnerability assessment. By leveraging publicly available network intelligence data, Nmap Freebuf provides a more comprehensive and contextually relevant understanding of target networks, enabling users to identify potential vulnerabilities, prioritize remediation efforts, and mitigate security risks more effectively. As the landscape of cyber threats continues to evolve, Nmap Freebuf remains an invaluable asset for those seeking to secure their networks and protect their digital assets.







Closure
Thus, we hope this article has provided valuable insights into Unlocking Network Security Insights: A Comprehensive Guide to Nmap Freebuf. We appreciate your attention to our article. See you in our next article!