Unlocking the Power of Memory-Mapped Files: A Comprehensive Guide to mmap
Related Articles: Unlocking the Power of Memory-Mapped Files: A Comprehensive Guide to mmap
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Unlocking the Power of Memory-Mapped Files: A Comprehensive Guide to mmap. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Unlocking the Power of Memory-Mapped Files: A Comprehensive Guide to mmap
- 2 Introduction
- 3 Unlocking the Power of Memory-Mapped Files: A Comprehensive Guide to mmap
- 3.1 Understanding the Mechanics of mmap
- 3.2 Benefits of Using mmap
- 3.3 Practical Applications of mmap
- 3.4 Exploring mmap in Detail
- 3.5 FAQs about mmap
- 3.6 Tips for Effective mmap Usage
- 3.7 Conclusion
- 4 Closure
Unlocking the Power of Memory-Mapped Files: A Comprehensive Guide to mmap

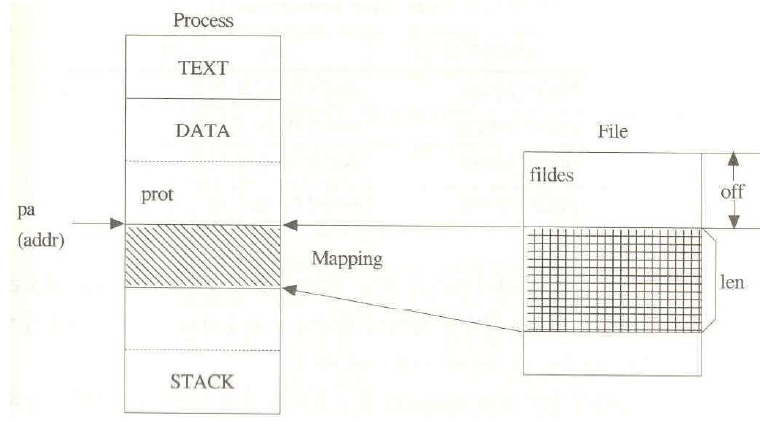
Memory-mapped files, often referred to as mmap, provide a powerful and efficient mechanism for interacting with files within a program’s address space. This technique bridges the gap between the virtual memory of a process and the physical storage of files, enabling seamless data access and manipulation. By mapping a file directly into memory, mmap eliminates the need for explicit read and write operations, significantly enhancing performance and simplifying data handling. This article delves into the intricacies of mmap, exploring its functionalities, benefits, and practical applications.
Understanding the Mechanics of mmap
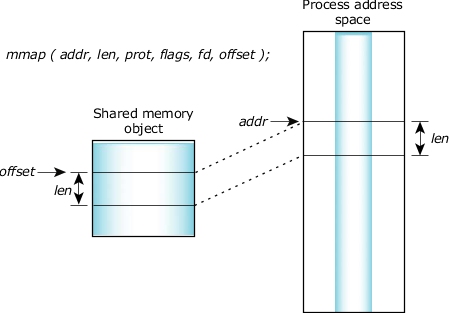
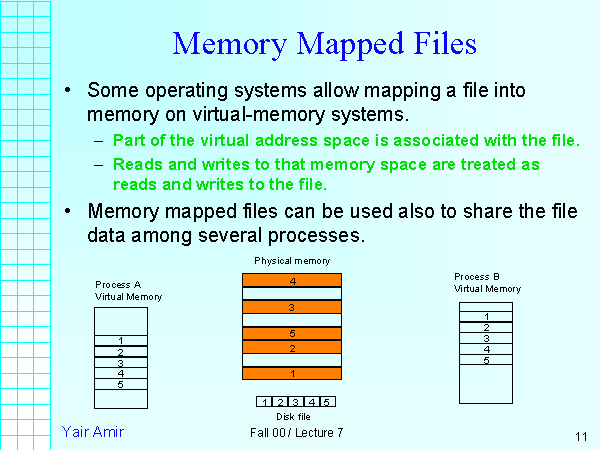
At its core, mmap establishes a direct connection between a file on disk and a region of a process’s virtual memory. When a file is memory-mapped, the operating system allocates a contiguous block of virtual memory that mirrors the file’s contents. This mapping allows the program to treat the file’s data as if it were directly in memory, accessing and modifying it without the overhead of traditional file I/O operations.
The process of memory-mapping a file involves several key steps:
-
File Opening: The program initiates the mapping process by opening the desired file. This step ensures that the file is accessible and ready for mapping.
-
Memory Allocation: The operating system allocates a region of virtual memory, sized to accommodate the file’s contents. This allocated region is reserved for the mapped file data.
-
Mapping: The operating system establishes a link between the file and the allocated virtual memory region. This link ensures that every modification to the memory region is reflected in the file on disk and vice versa.
-
Access: The program can now access and manipulate the file’s data through the mapped memory region, treating it as if it were in-memory data.
-
Unmapping: When the program no longer needs to access the file, it unmaps the memory region, releasing the allocated virtual memory and breaking the link between the file and memory.
Benefits of Using mmap
Employing mmap offers several advantages over traditional file I/O methods, making it a preferred approach in various scenarios:
-
Performance Enhancement: mmap significantly improves performance by eliminating the overhead associated with explicit read and write operations. Accessing data directly from memory is significantly faster than reading and writing to disk.
-
Simplified Data Handling: mmap simplifies data manipulation by allowing programs to treat file data as if it were in memory. This eliminates the need for complex file I/O operations, leading to cleaner and more efficient code.
-
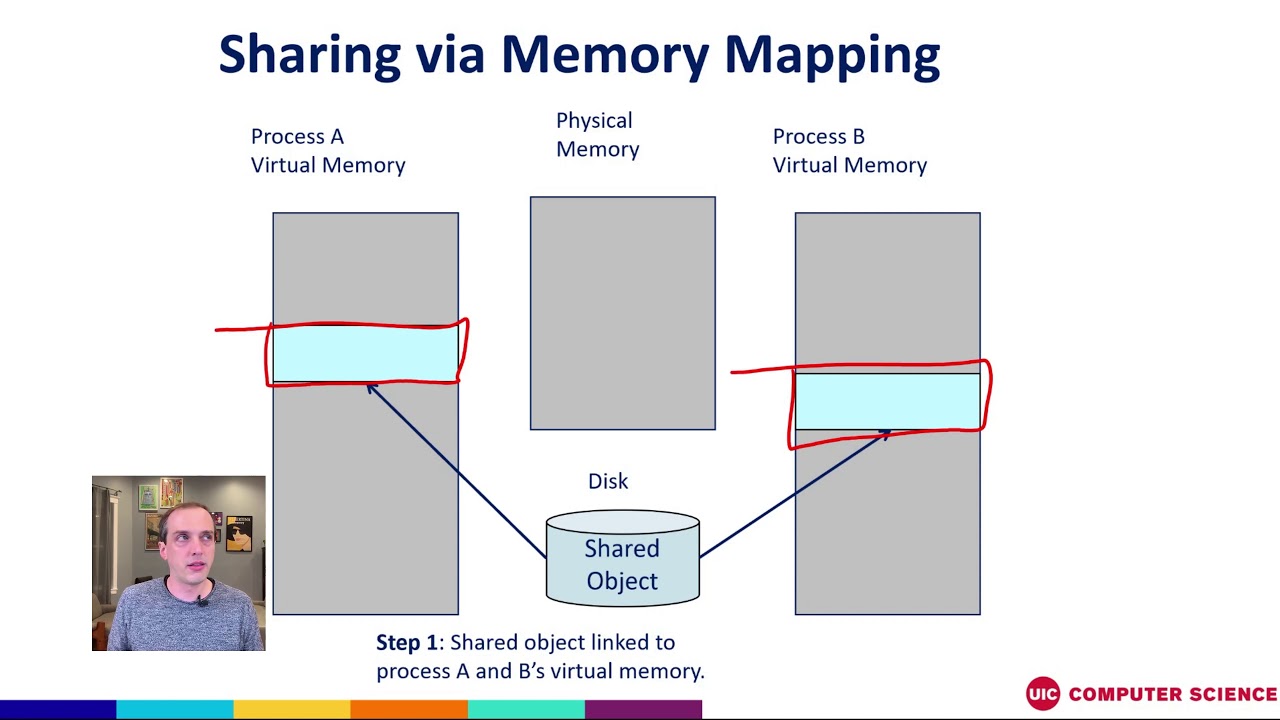
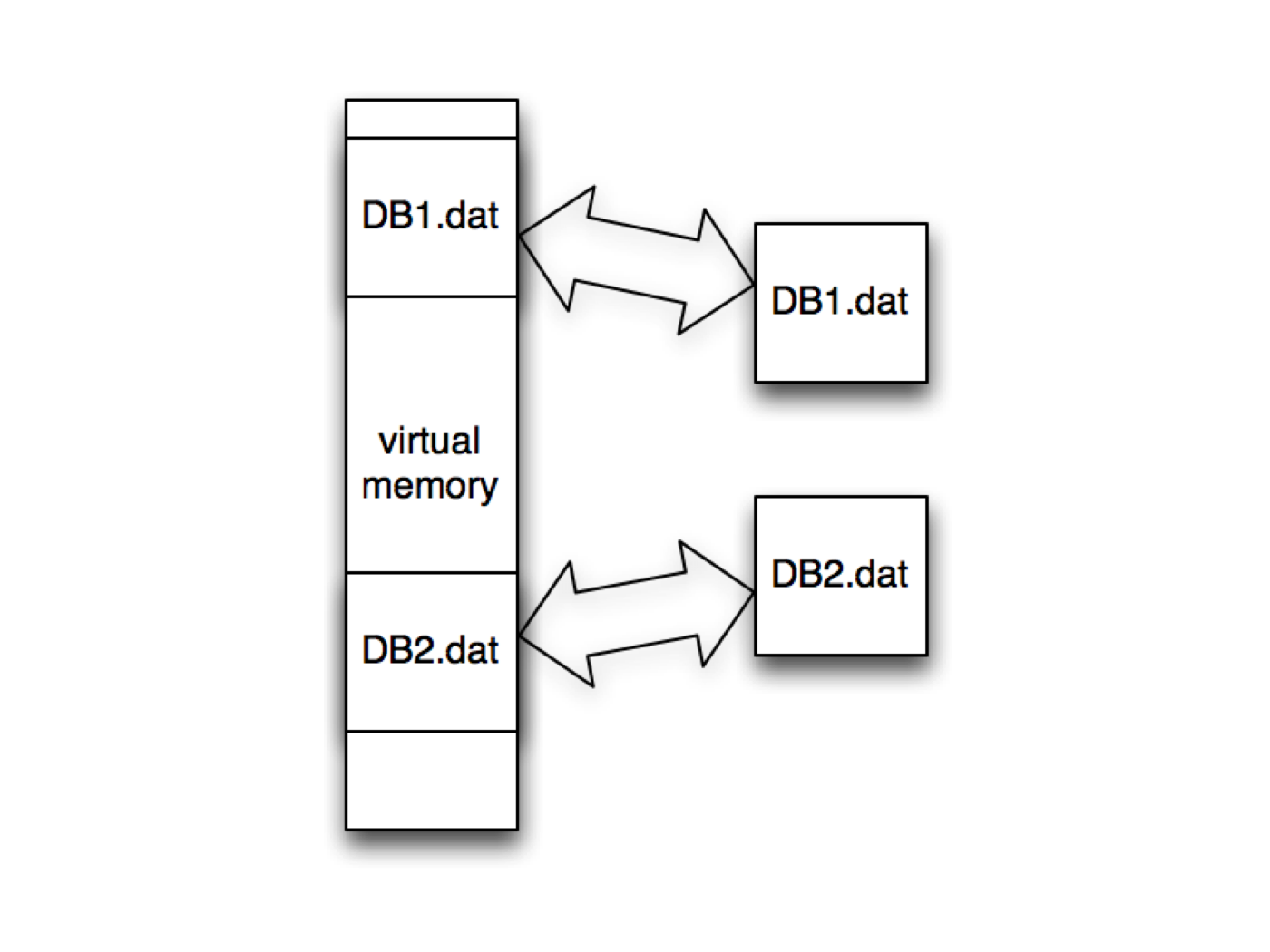
Shared Memory: mmap facilitates shared memory access between multiple processes. By mapping the same file into the memory spaces of different processes, they can access and modify the data concurrently, enabling efficient inter-process communication.
-
Memory-Mapped Files for Large Data: mmap is particularly effective when dealing with large files. Instead of loading the entire file into memory, mmap allows access to only the required portions, minimizing memory usage and improving performance.
Practical Applications of mmap
mmap finds widespread application in various domains, including:
-
Database Systems: Memory-mapped files are crucial in database systems for managing large data sets. By mapping data files into memory, databases can access and process data efficiently, leading to faster query execution and improved performance.
-
Image and Video Processing: mmap is extensively used in image and video processing applications. By mapping image and video files into memory, programs can manipulate and analyze the data directly, accelerating processing times and enabling real-time operations.
-
Text Editors and Word Processors: Text editors and word processors often employ mmap to manage large text files. By mapping the files into memory, they can provide fast and responsive editing capabilities, allowing users to navigate and modify documents seamlessly.
-
Web Servers: Web servers utilize mmap for caching static content. By mapping frequently accessed files into memory, servers can serve requests more quickly, reducing latency and improving overall performance.
-
Scientific Computing: mmap is essential in scientific computing applications that involve extensive data analysis. By mapping large datasets into memory, scientists can perform complex calculations and simulations efficiently, accelerating research and discovery.
Exploring mmap in Detail
To gain a deeper understanding of mmap, let’s delve into some of its key aspects and functionalities:
-
Mapping Modes: mmap offers various mapping modes that determine how the file is accessed and modified. The most common modes include:
-
MAP_SHARED: This mode allows multiple processes to share the same mapped file. Changes made by one process are immediately visible to other processes.
-
MAP_PRIVATE: This mode creates a private copy of the file in the process’s memory space. Changes made to the mapped region are not reflected in the original file.
-
MAP_ANONYMOUS: This mode allows creating anonymous memory mappings, not backed by a file. This is useful for inter-process communication and shared memory allocation.
-
-
Protection Flags: mmap provides protection flags that control the access permissions for the mapped memory region. These flags determine whether the region can be read, written, or executed.
-
File Offset: When mapping a file, the program can specify a specific offset within the file. This allows mapping only a portion of the file into memory, enabling efficient access to specific data segments.
-
Memory Allocation: mmap offers different memory allocation options, including:
-
MAP_FIXED: This option forces the mapping to be placed at a specific virtual memory address.
-
MAP_ANONYMOUS: This option allocates anonymous memory, not backed by a file.
-
-
Error Handling: Proper error handling is crucial when working with mmap. It is essential to check the return values of mmap and other related functions to ensure successful mapping and to handle potential errors gracefully.
FAQs about mmap
1. What are the advantages of using mmap over traditional file I/O?
mmap offers several advantages over traditional file I/O methods, including improved performance, simplified data handling, shared memory access, and efficient memory usage for large files.
2. Can mmap be used with multiple processes?
Yes, mmap can be used with multiple processes through the MAP_SHARED mapping mode. This mode allows processes to share the same mapped file, enabling efficient inter-process communication.
3. How does mmap handle file modifications?
When using the MAP_SHARED mode, changes made to the mapped memory region are automatically reflected in the file on disk. In the MAP_PRIVATE mode, changes are only applied to the private copy in memory.
4. Is mmap suitable for all types of files?
mmap is generally suitable for most types of files, but it is particularly effective for large files and those requiring frequent access. For small files or those with infrequent access, traditional file I/O methods may be more efficient.
5. What are the potential downsides of using mmap?
While mmap offers numerous benefits, it also has some potential downsides. These include:
* **Memory Usage:** mmap can consume significant memory, especially when mapping large files.
* **Complexity:** Using mmap effectively requires understanding its intricacies and handling potential errors.
* **Synchronization:** When using mmap with multiple processes, proper synchronization mechanisms are essential to avoid data corruption.Tips for Effective mmap Usage
-
Optimize Memory Usage: Carefully consider the size of the files you are mapping to minimize memory consumption.
-
Handle Errors Gracefully: Implement robust error handling mechanisms to handle potential errors during mapping and unmapping.
-
Use Appropriate Mapping Modes: Choose the appropriate mapping mode based on your application’s requirements.
-
Utilize Synchronization: When using mmap with multiple processes, employ appropriate synchronization techniques to ensure data consistency and avoid race conditions.
-
Consider Alternative Approaches: For small files or those with infrequent access, traditional file I/O methods may be more efficient.
Conclusion
Memory-mapped files provide a powerful and efficient mechanism for interacting with files within a program’s address space. By eliminating the overhead of traditional file I/O operations, mmap enhances performance, simplifies data handling, and enables shared memory access. Its applications span various domains, including database systems, image and video processing, text editors, web servers, and scientific computing. Understanding the intricacies of mmap and its various functionalities empowers developers to leverage its benefits effectively, leading to optimized performance and streamlined data management. As technology continues to advance, mmap will remain a vital tool for efficient file handling and inter-process communication, shaping the future of software development.


Closure
Thus, we hope this article has provided valuable insights into Unlocking the Power of Memory-Mapped Files: A Comprehensive Guide to mmap. We thank you for taking the time to read this article. See you in our next article!