Unveiling Network Secrets: Nmap on FreeBSD
Related Articles: Unveiling Network Secrets: Nmap on FreeBSD
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Unveiling Network Secrets: Nmap on FreeBSD. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Unveiling Network Secrets: Nmap on FreeBSD
- 2 Introduction
- 3 Unveiling Network Secrets: Nmap on FreeBSD
- 3.1 Understanding the Foundation: Nmap’s Capabilities
- 3.2 The Power of FreeBSD: A Robust Platform for Nmap
- 3.3 Practical Applications: Putting Nmap to Work
- 3.4 FAQs: Addressing Common Questions
- 3.5 Tips for Effective Nmap Usage
- 3.6 Conclusion: Nmap – An Indispensable Tool for Network Exploration
- 4 Closure
Unveiling Network Secrets: Nmap on FreeBSD

Nmap, the Network Mapper, stands as a cornerstone of network security auditing and exploration. This powerful and versatile tool, available on a multitude of platforms including FreeBSD, empowers network administrators, security professionals, and researchers to gain a comprehensive understanding of network infrastructure and its vulnerabilities. This article delves into the intricacies of utilizing Nmap on FreeBSD, highlighting its capabilities, advantages, and practical applications.
Understanding the Foundation: Nmap’s Capabilities
At its core, Nmap operates by sending specially crafted packets to target systems and analyzing the responses received. This process, known as network scanning, enables Nmap to gather valuable information about the network, including:
- Host Discovery: Identifying active hosts on the network, their IP addresses, and MAC addresses.
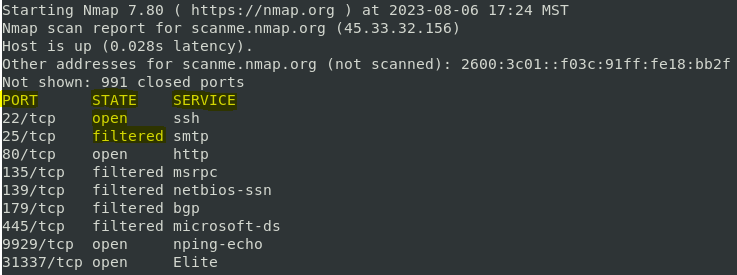
- Port Scanning: Determining which ports on a host are open and the services running on those ports.
- Operating System Detection: Identifying the operating system running on a host based on its response patterns.
- Service Version Detection: Identifying the specific version of a service running on a port.
- Network Mapping: Creating a visual representation of the network topology, showcasing connections between hosts.
- Vulnerability Scanning: Identifying potential security weaknesses in services and applications.
Nmap’s versatility stems from its extensive range of scan types, each tailored to specific objectives. Common scan types include:
- SYN Scan: A stealthy scan that avoids triggering intrusion detection systems by only sending a SYN packet and not completing the TCP handshake.
- Connect Scan: A straightforward scan that establishes a full TCP connection to each port, revealing open ports but potentially triggering intrusion detection systems.
- UDP Scan: A scan specifically designed to probe UDP ports, identifying open ports and services running on them.
- Ping Scan: A basic scan that utilizes ICMP packets to determine host availability without revealing much information about the host.
- Version Scan: A scan that attempts to identify the version of a service running on a port, providing valuable insights into potential vulnerabilities.
The Power of FreeBSD: A Robust Platform for Nmap
FreeBSD, a Unix-like operating system renowned for its stability, security, and performance, provides an ideal environment for Nmap. Its robust network stack and extensive command-line tools make it an excellent choice for network administrators and security professionals seeking to leverage Nmap’s full potential.
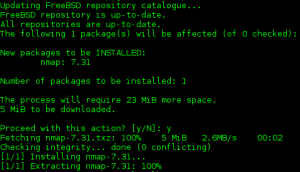
Installing Nmap on FreeBSD is straightforward, typically achieved through the package manager. The pkg command provides a user-friendly interface for installing, updating, and removing software packages, including Nmap.
# pkg install nmapOnce installed, Nmap is accessible through the command line. Running nmap -h displays the comprehensive help menu, outlining all available options and their functionalities.
Practical Applications: Putting Nmap to Work
Nmap’s capabilities translate into a wide range of practical applications, empowering users to:
- Network Inventory and Management: Nmap can quickly scan a network to identify all active hosts, their operating systems, and the services they offer. This information is essential for network administrators to effectively manage their infrastructure, ensuring optimal performance and security.
- Security Auditing: Nmap facilitates thorough security audits by identifying open ports, vulnerable services, and potential attack vectors. This allows security professionals to prioritize remediation efforts and strengthen network defenses.
- Vulnerability Research: Nmap’s ability to detect service versions and identify common vulnerabilities makes it a valuable tool for researchers seeking to understand and exploit security weaknesses.
- Network Troubleshooting: When network connectivity issues arise, Nmap can pinpoint the source of the problem by identifying unreachable hosts, blocked ports, or malfunctioning services.
- Host Discovery and Enumeration: Nmap enables the discovery of hidden hosts and the enumeration of their services, valuable for penetration testing and reconnaissance.
FAQs: Addressing Common Questions
Q: Is Nmap legal to use?
A: Nmap itself is a legitimate tool used for network management and security auditing. However, using it for malicious purposes, such as unauthorized scanning or denial-of-service attacks, is illegal. It is crucial to use Nmap responsibly and ethically, adhering to local laws and regulations.
Q: Can Nmap be used for penetration testing?
A: Yes, Nmap is a valuable tool for penetration testing, enabling the discovery of potential vulnerabilities and attack vectors. However, it is essential to obtain explicit permission from the target organization before conducting any penetration testing activities.
Q: How can I avoid triggering intrusion detection systems (IDS) while using Nmap?
A: Nmap offers various scan types designed to minimize detection, such as SYN scans and stealth scans. Additionally, customizing scan timings and using IP spoofing techniques can further reduce the likelihood of triggering IDS alerts.
Q: What are some advanced Nmap techniques?
A: Nmap offers a wide array of advanced techniques, including:
- Script Scanning: Running custom scripts to perform specific tasks, such as identifying specific vulnerabilities or gathering detailed information about services.
- Service Fingerprinting: Identifying specific service versions and configurations based on their response patterns.
- Network Mapping with Nmap NSE: Utilizing Nmap’s Network Security Engine (NSE) to perform complex tasks, such as network discovery, vulnerability scanning, and service enumeration.
Tips for Effective Nmap Usage
- Start with Basic Scans: Begin by performing simple scans to get a general understanding of the network and identify potential targets.
- Use Specific Scan Types: Tailor your scans based on your objectives, utilizing appropriate scan types like SYN scans for stealth or UDP scans for UDP port analysis.
- Leverage Nmap’s Scripting Capabilities: Utilize Nmap scripts to automate tasks and gather specific information, such as identifying open ports or detecting common vulnerabilities.
- Experiment with Nmap Options: Explore Nmap’s extensive options to customize scans and optimize results, such as adjusting scan timings, specifying target ranges, or using IP spoofing techniques.
- Document Your Findings: Record scan results meticulously, including timestamps, target information, and identified vulnerabilities. This documentation is essential for reporting and remediation efforts.
Conclusion: Nmap – An Indispensable Tool for Network Exploration
Nmap, readily available on FreeBSD, empowers network administrators, security professionals, and researchers to gain a comprehensive understanding of network infrastructure and its vulnerabilities. Its versatile capabilities, including host discovery, port scanning, operating system detection, service version identification, and vulnerability scanning, make it an indispensable tool for network management, security auditing, penetration testing, and troubleshooting. By leveraging Nmap’s features and techniques responsibly and ethically, users can enhance network security, optimize performance, and proactively address potential threats.




Closure
Thus, we hope this article has provided valuable insights into Unveiling Network Secrets: Nmap on FreeBSD. We appreciate your attention to our article. See you in our next article!